It started with a simple mistake, a confidential file shared through an unsecured link. Within hours, sensitive client information was in the wrong hands.
Sound dramatic? Unfortunately, it’s not. Document-related breaches are far more common than you’d expect. A report by Astra reveals that a business is targeted by a cyberattack every 39 seconds.
The real question is: How secure are your own confidential files?
If you’re unsure, it’s time to find out. In this guide, we’ll examine potential risks, their consequences, and explore strategies to secure confidential documents from costly risks.
Key Takeaways:
- Confidential documents include personal, corporate, legal, and government records, which could cause harm if leaked.
- Begin with basics: strong passwords, watermarks, access control, and version tracking.
- Layer up with advanced protection: encryption, digital signatures, audit trails, and QR-based verification.
- Classify documents by sensitivity, and use both physical and digital measures for complete security.
Let’s begin!
A. What are confidential documents?

Confidential documents are files or records that contain sensitive information not meant for public access.
These documents typically hold details that, if exposed, could lead to identity theft, legal issues, financial loss, or even national security threats, depending on the context.
Think of things like medical reports, employee records, proprietary contracts, or classified intelligence briefs.
Each serves a specific purpose, but what they all have in common is the need for strict access control.
These documents can be divided into four major categories based on the type of sensitivity involved:
1. Personal documents
These typically include Personally Identifiable Information (PII), means data that can directly or indirectly identify an individual. That includes:
- Social security numbers or national IDs
- Health records
- Bank and credit card statements
- Tax returns
- Educational transcripts
- Utility bills with address and contact info
Even a resume can be considered confidential if it includes your full address, phone number, or references. This kind of information is gold for identity thieves.
A stolen ID and date of birth are often all it takes to open fake bank accounts, file fraudulent tax returns, or even commit insurance scams. What’s worse is that victims often don’t know it’s happening until the damage is done.
2. Corporate documents
These are internal documents that, if leaked, can disrupt business operations or give competitors an unfair edge. Examples include:
- Financial statements and revenue reports
- Intellectual property (IP) like source code, product designs, or trade secrets
- Strategic plans and pricing models
- Client or vendor contracts
- Employee records and payroll data
Many corporate frauds and data leaks begin with an insider sharing or stealing sensitive business information.
3. Legal documents
These involve binding agreements and processes that are often protected by confidentiality laws or clauses. Examples include:
- NDAs (non-disclosure agreements)
- Legal contracts and settlement terms
- Patent applications
- Confidential correspondence between lawyers and clients
- Private court filings
Unauthorized access to legal records can lead to serious consequences, both for the parties involved and for those responsible for keeping them secure.
4. Government documents
These include sensitive information created or held by government bodies. These documents range from restricted to top-secret and can include:
- Intelligence reports
- Classified military strategies
- Diplomatic cables
- Personal data collected by government agencies
Some of these, if leaked, don’t just affect one organization or person—they can have international consequences.
B. What are the risks of leaving confidential documents unprotected?

When confidential files fall into the wrong hands, the consequences go way beyond embarrassment. Let’s look at what happens when your documents aren’t protected properly.
Whether it’s a curious employee or a hacker halfway across the world, unauthorized access happens when someone gains entry to data they were never meant to see.
1. Data breaches
When a document gets exposed to someone who shouldn’t see it, that’s a data breach.
Whether it’s internal snooping or an external cyberattack, the outcome is the same: sensitive information ends up in the wrong hands.
And from there, it can snowball into identity theft, financial fraud, or even corporate espionage.
Take the MOVEit breach in 2023, for example. It started with a vulnerability in a popular file transfer tool. The ransomware group Cl0p exploited it to access data from over 2,700 organizations, including the BBC and British Airways. In the end, personal information of more than 93 million people was exposed. All because of one unpatched flaw in third-party software.
2. Financial penalties
Most industries today are governed by strict data protection laws. And these laws come with teeth.
If you’re a business, you’ve probably heard of GDPR in Europe, HIPAA for healthcare in the U.S., or PCI-DSS if you deal with credit card payments. These aren’t just best practices, they’re legal obligations.
And non-compliance? That can cost you millions or sometimes even billions, depending on the extent of the damage.
Just look at TikTok. In 2023, the platform was fined €345 million under GDPR for mishandling children’s data, like setting accounts to public by default and not being transparent enough. It’s a clear reminder that non-compliance doesn’t just hurt your reputation, it can burn a deep hole in your pocket too.
3. Competitive disadvantage
When sensitive business documents get exposed, it goes beyond just being a privacy issue. It’s a direct hit to your market position.
Competitors can see exactly what you’re building, mimic your strategies, or even copy your IP. The fallout isn’t always instant, but it can quietly chip away at your competitive edge in ways that are hard to reverse.
In 2017, a former Waymo (Google’s self-driving car unit) engineer walked off with over 14,000 confidential files and joined Uber. Those files gave Uber a major shortcut in developing its LiDAR tech. The result? A $245 million lawsuit settlement, just because one employee’s move nearly shifted the balance in an entire industry.
4. Reputation damage
Trust is hard-earned and easily lost. So, when a confidential document leaks, it dents your credibility.
People don’t forget data leaks. Customers get nervous. Partners hesitate. Investors lose confidence. And even if you fix the breach, cleaning up your reputation can take years.
Remember the 2014 Sony Pictures hack? Thousands of internal emails, scripts, and even unreleased films were leaked. But what hurt most was the exposure of private conversations and exec-level commentary. It damaged relationships, cost careers, and left a long-lasting dent in Sony’s public image.
5. Operational disruption
When a document breach happens, it doesn’t just trigger damage control or PR crises. It can literally bring your business to a standstill. Systems might need to be taken offline. Internal investigations can delay critical workflows. Teams are forced to drop everything and respond.
And here’s the part most people overlook: the time, energy, and productivity lost during that chaos often go unmeasured.
C. 4 Basic ways to secure confidential documents
1. Password protection for digital files
One of the easiest and, honestly, most underrated ways to secure your digital documents is with password protection. It might seem basic, but it acts as a crucial first line of defense.
This method protects your files from casual snooping, unauthorized sharing, and even from being opened if your device gets lost or hacked.
Of course, it won’t stop a determined cybercriminal with advanced tools, but for everyday threats and internal mishandling, it does the job well.
The key? Use strong and non-repetitive passwords. Avoid “1234” or your dog’s name. Instead, go for passphrases like “Green*Leaf$77CleverBird.”
Here’s how you can set it up:
For Microsoft Word, Excel, or PowerPoint (Windows & Mac):
Open the file you want to protect > File > Info > Protect Document (or Workbook/Presentation) > Encrypt with Password > Enter password > OK
Note: If you use Google Workspace, you won’t find a password option. Google Docs uses role-based access control, which we’ll cover in the next section.
For PDF files using Adobe Acrobat Pro:
Open the PDF > File > Protect Using Password > Choose whether to password-protect for viewing or editing > Set password > Confirm
These steps may seem simple, but they lay the groundwork to effectively secure confidential documents in everyday workflows.
2. Role-based access control
Think of role-based access control as the “need-to-know” rule for your documents. Instead of giving everyone full access, you assign roles like viewer, editor, or owner, and let people see only what they’re supposed to.
It’s a smarter way to limit exposure and reduce the risk of accidental leaks or intentional misuse. This is especially useful in workplaces where multiple teams interact with sensitive files. And you want visibility without risk, while still working to secure confidential documents.
For example, your finance team doesn’t need access to HR documents, and interns don’t need editing rights on your legal contracts.
How to set it up:
On Google Docs, Sheets, or Slides:
Open the file > Click Share (top right) > Enter email addresses or copy the shareable link > Next to each person’s name or the link option, choose their role: Viewer, Commenter, or Editor > Send
Note: Click the settings icon to disable options like downloading, copying, or printing for viewers and commenters. This is especially helpful when you want visibility without risk.
On Microsoft OneDrive or SharePoint:
Right-click the document > Share > Choose People you specify can view > Enter emails > Click the pencil icon to switch between Can edit or Can view > Send
3. Watermarking
Think of watermarking and labeling as visual reminders. They’re not just cosmetic—they tell everyone handling the document that it’s sensitive and must be treated carefully.
Watermarks like “Confidential,” “Do Not Copy,” or “Internal Use Only” act as a deterrent. They make it harder for someone to misuse or redistribute a document without accountability.
These tactics don’t prevent access, but they discourage leaks and misuse.
How to add a watermark:
Microsoft Word (Windows & Mac):
Open the document > Go to Design tab > Click Watermark > Choose a built-in watermark (like “Confidential”) or select Custom Watermark to add your own text or image > Apply
PDF files using Adobe Acrobat Pro:
Open PDF > Click Edit PDF > Choose Watermark > Add > Type your watermark (e.g., “Confidential – Do Not Share”) > Set its position and opacity > Click OK
4. Lockable cabinets and safes
We often get so caught up in digital threats that we forget that physical document protection still matters. A lot. Many businesses still handle contracts, identity proofs, blueprints, and other sensitive paperwork in hard copy.
Make sure confidential papers are stored in lockable cabinets with limited key access. For highly sensitive files, use proper safes rather than makeshift storage.
Physical security also plays a vital role in protecting personal and confidential information, especially in sectors like healthcare, legal, or finance.
Pro Tip: Choose a safe that’s fireproof, waterproof, and if possible, temperature-controlled. That way, your documents are protected not just from unauthorized access, but also from natural disasters.
D. 5 Advanced Methods to Secure Confidential Documents
Once you’ve covered the basics, it’s time to explore more sophisticated ways to secure confidential documents using modern tools and verification systems.
1. QR Code verification
QR Codes aren’t just for menus or payments anymore, they’re becoming a powerful layer of document security.
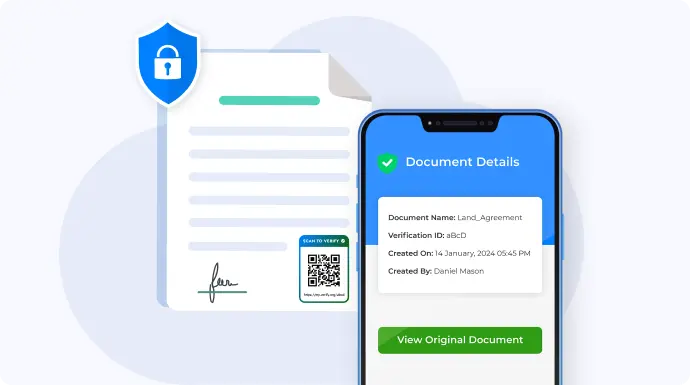
When added to a document, a QR Code can link to a secure, original version hosted by the issuer. This allows anyone who scans it to instantly verify its authenticity and check for tampering (see Section E for how it works).
Where does this help? Anywhere you need to prove a document is original like contracts, certificates, offer letters, or reports.
For example, Many universities now place QR Codes on degree certificates. When scanned, they lead to the official version on the university’s site, making it easy for employers and institutions to spot fake degrees.
Note: Not all QR Codes are built for security. Generic ones that link to public URLs aren’t secure. Go with QR Code security providers built for this purpose, like QR Mark (for ease and scale), Qryptal (for blockchain-based validation), or Certifier (if you’re focused on certificates).
2. Encrypting files and folders
If password protection is your basic lock, encryption is the vault. It scrambles your files into unreadable code that only someone with the right decryption key can access.
Even if someone gets their hands on the file, without that key, it’s just gibberish. This makes encryption a must for storing or sharing highly sensitive documents, especially over email or cloud platforms.
Pro tip:
Both Windows and macOS have built-in tools to help with this:
- On Windows, use BitLocker for drives or EFS (Encrypting File System) for individual files/folders.
- On Mac, use FileVault for disk encryption or Disk Utility to create encrypted folders.
Also, many popular tools like Adobe Acrobat, Microsoft Office, and even 7-Zip offer file-level encryption with strong algorithms like AES-256.
Use encryption when storing legal agreements, financial reports, research IP, or anything you can’t afford to lose or expose. It’s an essential line of defense and unlike a password, it can’t be bypassed easily.
3. Multi-factor authentication (MFA)
If someone gets your password, which is pretty simple to break for a bad actor, the game’s over. But if you use Multi-Factor Authentication (MFA), it adds an extra step, like a one-time code sent to your phone or an approval through an app.
This makes sure it’s really you accessing the data, not someone pretending to be you. Even if someone gets your password, they can’t get in without that second factor.
Most cloud platforms today, including Google Workspace, Microsoft 365, Dropbox, etc., offer MFA as a standard feature.
Turning it on for accounts where sensitive documents are stored is one of the simplest yet most effective ways to keep out intruders.
Pro tip: Use app-based authenticators like Google Authenticator, Microsoft Authenticator, or Authy instead of SMS for better security. SMS codes can be intercepted, but apps are far more secure.
4. Audit trails and access logs
Audit trails and access logs tell you who accessed a document, when, and what they did with it. They act like a surveillance camera for your files and track every interaction in the background.
With these logs, you can detect suspicious activity early, spot unauthorized access, and even investigate leaks if something goes wrong.
Most Document Management Systems (DMS), Google Workspace (via Admin Console), and Microsoft SharePoint already include access logs by default.
On Google Workspace (Admin only):
Go to admin.google.com > Reports > Audit Log > Choose “Drive” > You’ll now see who accessed what, when, and from where. You can also filter by user, document type, or time.
On Microsoft 365 (Admin only):
Go to Microsoft Purview compliance portal > Audit > Start recording user and admin activity (if not already active) > Use search bar to find activities (like file access, edits, deletions) by user, date, or event type.
5. Digital signature tools
Don’t confuse digital signatures with simple e-signatures. While e-signatures are just visual marks, like typed names or scanned images, a digital signature is far more secure.
It uses encryption to prove the document really came from you. It also locks the file so that even the tiniest change breaks the seal and makes the signature invalid.
To use a digital signature, you’ll need a digital certificate. It’s a verified ID issued by a trusted Certificate Authority (CA). Without it, the signature won’t be legally valid or verifiable.
Once you have the certificate, tools like DocuSign, Adobe Sign, and SignEasy can help you easily apply digital signatures to your documents.
E. How QR Codes can help secure confidential documents
As we briefly touched on earlier, QR Codes are now playing a big role in document security. But why the sudden surge in popularity?
Well, here’s what makes them so effective:
1. Instant verification
Anyone with a smartphone can scan the QR Code and instantly access the verified version of the document. This gives recipients a quick and reliable way to confirm that what they’re looking at is genuine, without needing to call or email the issuer.
2. Stops tampering
Each document includes a unique QR verification image that can only be generated through secure dashboard access.
Even if someone tries to morph or reuse the QR on a tampered file, it won’t fool the system. Tools like QR Mark ensure the QR always leads to the original version hosted by the document owner. So any edits or forgery attempts are immediately exposed.
3. Proves authenticity
The QR Code links directly to a secure URL belonging to the verified issuer (like a company’s or institution’s domain).
This makes it easy to trace the document back to its trusted source and instantly spot any unauthorized copies.
4. No extra tools needed
You don’t need any special hardware, software, or apps to make this work. All it takes is a camera phone to scan and verify, making it accessible even for those with zero technical know-how.
5. Affordable
Compared to many advanced document security methods like encryption suites, blockchain systems, or holographic labels, QR Codes offer a much more budget-friendly solution. Especially when you need to secure documents at scale.
6. You stay in control
You can deactivate a QR Code from your dashboard once the document has served its purpose.
7. Works for both digital and printed documents
Whether it’s a PDF sent via email or a paper certificate handed over in person, the QR Code works seamlessly across formats.
And over everything else, they’re incredibly easy to use. You don’t need to understand encryption, manage keys, or outsource to expensive vendors. Just generate, place, and protect.
Here’s how to do it, I’m using QR Mark for reference (but you can use any QR Code security tool):
Step 1. Log in or sign up on QR Mark.
Step 2. Go to Settings and add your custom domain. Once added, you’ll need to verify domain ownership.
This is a one-time step that ensures only you can generate verifications linked to your domain. It’s what prevents others from mimicking your documents.
Step 3. Head to the Verifications tab and click Create Verification.
(Optional: Go to “Integrations” first to install the Google Workspace or Microsoft 365 add-ons. This lets you generate verifications directly while creating the document.)
Step 4. Upload your PDF by selecting the source.
Choose your verified custom domain, and this will be the domain shown when someone scans the QR Code.
Step 5. Give your document a name (for internal tracking).
Step 6. Choose whether you want the QR verification image on the current page or all pages.
Step 7. Click Generate Verification Image and adjust its placement on the document.
Step 8. Finally, click Export PDF to download your secured file.
F. Secure confidential documents in your team or organization

1. Define and Enforce a Document Retention Policy
Not all documents need to be kept forever. Holding on to outdated or unnecessary files only increases your risk of exposure.
A document retention policy outlines how long different types of documents should be stored and when they should be disposed of.
2. Ensure secure disposal of confidential documents
Disposing of documents the right way is just as important as protecting them while in use. Simply deleting a file or tossing paper into a bin isn’t enough.
For digital files, use secure deletion tools that overwrite the data and make it unrecoverable. This is especially important for confidential documents stored on old hard drives, USBs, or cloud folders.
For physical documents, shredding is common, but for higher sensitivity, consider incineration (complete burning) or pulping (turning paper into a slurry so it’s unreadable and unrecoverable).
3. Use non-disclosure agreements (NDAs)
NDAs legally bind employees, vendors, or partners from disclosing sensitive information.
Always have signed NDAs in place when working with confidential data, and make sure they cover the right scope, duration, and jurisdictions.
4. Train employees on document security
Even the best systems can be undone by human error. Whether it’s sharing access accidentally or falling for phishing scams, untrained staff can be the weakest link.
Regular training, especially during onboarding and at intervals, is key. Teach employees about password hygiene, spotting phishing attempts, and handling confidential documents securely (both online and offline).
5. Align third parties with your security standards
If vendors, contractors, or freelancers handle your confidential documents, their practices become your risk. Before sharing any data, check if their security protocols align with yours.
Use third-party risk assessments, share your document security policy, and, where possible, use platforms where you control document access rather than sending files outright.
G. FAQs

1. What information should you keep confidential?
Anything that can be used to identify, exploit, or harm someone or something should be considered confidential.
That includes personal data like Social Security numbers, health records, passwords, financial details, employee files, legal documents, business strategies, client lists, proprietary research, and contract terms.
The key question is: If this got into the wrong hands, what could go wrong? If the answer is “a lot,” then it’s confidential.
Also, not all confidential information is obvious. Internal emails, pricing models, or even meeting notes can contain sensitive context you wouldn’t want leaked.
2. Why is it important to maintain confidentiality of records?
Confidentiality protects more than just privacy. It protects trust, compliance, and competitive advantage.
When you handle sensitive records, you’re responsible for the safety of the people or entities behind them. A single leak can cost millions in fines, break client relationships, or expose your company to lawsuits. In regulated industries like healthcare or finance, it’s not just important, it’s the law.
Beyond legal and financial consequences, there’s also brand reputation. One breach, and you’re seen as careless. That’s hard to recover from.
3. How do you deal with confidential information?
Treat it with intention and care. Limit who has access, keep it secure, digitally and physically, and avoid discussing it casually.
Use secure systems for sharing or storing it, and make sure it’s clearly labeled so others treat it accordingly. And when it’s no longer needed, dispose of it safely, not just by deleting or trashing it.
4. How to keep confidential information safe?
Use secure tools, share only when necessary, and think privacy-first. Store data on encrypted platforms, use strong passwords with two-factor authentication, and never leave sensitive info unattended physically or online.
It’s about creating habits where security becomes part of the way you work.
Next steps
If you’ve made it this far, you already know how high the stakes are. Start by identifying the most sensitive documents you handle, whether personal, legal, corporate, or governmental. Don’t try to fix everything at once.
Instead, prioritize the biggest risks and begin applying the basics: strong passwords, proper access controls, watermarks, and physical safeguards.
Once that’s done, look into more advanced tools like encryption, secure sharing platforms, and tamper-proof technologies like QR Mark. Each step you take strengthens your overall defense.


Leave a Reply