Imagine your company is finalizing a crucial vendor agreement. You share the document internally, assuming it’s secure. A few days later, you discover that an unauthorized party has accessed it, altered key terms, and used the information for their benefit.
Alarming, right? That’s where document security comes in to safeguard important documents.
This blog will break down everything from what it means to the best ways to protect your digital and physical documents.
Let’s begin!
A. What is document security?
Document security refers to the practice of guarding sensitive documents from improper access, modification, theft, or misuse. It guarantees that only the appropriate individuals are able to view or modify a document.
Did you know? In only the third quarter of 2024 alone, 422.61 million data records leaked in breaches globally.
Given the ever-changing nature of contemporary data security threats, organizations need to upgrade their document protection and train staff on new security protocols.
It can produce very grave risks if left unchecked including:
- Unauthorized Access–When an unauthorized individual acquires a document, it can lead to leaks, abuse, or even company espionage.
- Data Breaches – Even if security exists, but it’s compromised, then hackers can breach it. They often find and exploit vulnerabilities like weak encryptions, simple passwords, or outdated software. This may result in sensitive data getting leaked or even ransomware where they demand money to restore data.
- Data Manipulation – If someone modifies a document without consent, fake duplicates can be prepared and utilized for fraud or even for personal advantage.
B. Why document security is crucial
1. Prevents data breaches and unauthorized access
Including document security makes breach attempts futile, but the measure of protection varies with the need.
Some documents are secured to limit visibility, some to avoid unauthorized copies, and others to keep their integrity intact without alteration.
2. Helps maintain compliance with legal and regulatory requirements
Governments across the globe have strict data handling policies that organizations have to adhere to. Noncompliance can result in legal repercussions and severe damage to reputation.
For instance, a hospital that does not keep patient medical records confidential may face legal action against it under HIPAA (Health Insurance Portability and Accountability Act).
3. Ensures nonrepudiation
Nonrepudiation is when the party responsible for an action or a change cannot deny it. This makes stakeholders accountable and minimizes the possibility of internal threats.
It can be done through features such as version control, editing trails, or digital signatures (discussed later).
But does every document require the maximum level of security? No!
C. Types of documents that require security
Not all documents carry the same level of risk, but some require strict security measures due to their sensitivity.
A sensitive document is any file or record having confidential information that is supposed to be known by limited people. If accessed wrongfully, it could cause financial or reputational loss to individuals, businesses, or governments.
1. Financial documents
These could be business financial reports, tax returns, audit reports, or investment information. Unauthorized access or tampering with these can result in financial fraud, insider trading threats, or competitive loss.
2. Public-facing documents
These documents, such as bills, warranty certificates, and insurance claims, are issued in a customer’s name and require security to verify authenticity. If left unprotected, they can be misused for fraud.
3. Legal documents
This involves documents such as contracts, non-disclosure agreements (NDAs), license agreements, court records, and even company policies. These, when unethically changed, would result in lawsuits, regulatory penalties, and reputation loss.
4. Employee records
Employees are the most important asset of an organization, and it is a prime responsibility to keep their data secure. A leak of data can lead to identity theft, inappropriate associations with the company, or monetary loss for the individual as well as the company.
5. Intellectual property documents
These include documents that include major innovations of a company like patents, proprietary algorithms, trade secrets, product designs, business strategies, and R&D documents. Cyber espionage or insider threats targeting IP can cost companies billions.
6. Customer and client information
This includes personal and transactional records of clients and customers. A data leak not only puts them at risk of identity theft but also exposes your business to reputational damage and legal penalties under data protection laws. Some key data protection laws and frameworks include the following.
GDPR – One of the most stringent privacy laws, requiring businesses to follow GDPR regulations to protect EU citizens’ personal data and ensure it isn’t misused.
ISO 27001 – A globally recognized standard that helps businesses implement strong security controls as outlined in the ISO 27001 framework to protect against cyber threats.
SOC 2 – Developed by AICPA, it ensures SaaS and cloud-based service providers maintain high standards of security, availability, and confidentiality.
So, ensure you select a vendor like QR Mark for your document security that is certified in these frameworks. This guarantees regulatory compliance and assures you that your data is in safe hands.
Now you know which documents need protection. Next, let’s look at the methods that help secure them.
D. Methods for ensuring document security
Methods of document security vary from password protection to the management of how a document is stored, shared, and accessed during its lifecycle.
The format doesn’t matter in securing documents, you can secure a PDF, DOCX, XLSX, PPTX, and more.
You can use one method or even a combination of a few methods depending on the needs and the importance of the document.
1. Encryption
Encryption converts digital documents into an unreadable format that can only be decoded with the correct decryption key.
Here’s how it works: the original document is processed through an encryption algorithm, which turns it into a cipher using an encryption key. It requires the correct key to decrypt and read the content ensuring digital document security.
For example, after a major data breach in 2008 that exposed sensitive banking details, Heartland Payment Systems adopted end-to-end encryption (E2EE). This ensured cardholder data stayed encrypted throughout transactions, making it unreadable to unauthorized parties.
Pros:
– Even if intercepted, encrypted files remain unreadable.
– Protects data both at rest (saved files) and in transit (emails, cloud sharing).
Cons:
– If the encryption key is lost, recovery is difficult and resource-intensive.
– Not usable for physical documents
– Requires specialized software and personnel to implement
– Weak encryption algorithms are vulnerable to breaches
As world-renowned security technologist Bruce Schneier states, “Strong encryption means unbreakable encryption. Any weakness in encryption will be exploited—by hackers, by criminals, and by foreign governments.“
2. QR Codes
QR codes are increasingly being used to secure documents by authenticating their origin and verifying their integrity.
They are especially useful for documents issued by companies to customers and clients, such as invoices, certificates, warranty documents, and contracts.
Upon scanning, the QR Code takes the user to a verified page from the issuer, with information such as the creation date, a unique verification ID, and other factors to verify authenticity.
For example: Auburn Institute of Maritime Training wanted to tackle the issue of fake completion certificates being issued in their name. They used QR Mark to add a QR verification image on their certificates, ensuring the origin and authenticity were easily identifiable.
Pros:
– Helps prevent document fraud and counterfeiting
– QR codes can be scanned using any smartphone
– Can protect both digital and physical copies of documents
Cons:
– End-users must have internet access for verification
– Requires a stable hosting platform to maintain long-term accessibility
3. Document rights management (DRM)
DRM is a technology that gives you control over a document’s access, usage, modification, and distribution.
Beyond just encrypting files, it allows for advanced access controls like time-based restrictions (e.g., expires after 7 days), printing control, and forwarding restrictions.
DRM is increasingly used to protect intellectual property, especially copyrighted or patented materials, as they require strict security.
For example: Amazon Kindle needed to protect its e-books from piracy and unauthorized distribution to avoid losing revenue. They implemented a proprietary DRM system that encrypts e-books, ensuring only the buyer can access them. This Kindle DRM prevents copying and sharing, while also letting publishers set rules like restricting printing or lending.
Pros:
– Streamlines and simplifies security management for multiple documents
– Enables the owner to revoke access anytime remotely
Cons:
– Requires specialized software or integration into document management systems
– DRM-protected files need compatible software for access
4. Password protection
Password protection provides a virtual wall of protection by asking for a password prior to opening a document. Anytime someone attempts to open the file, they must provide the right password in order to access it.
A 2024 LastPass report found that 81% of company data breaches were due to weak or reused passwords.
Hence, it’s suggested to use passphrases like ‘BlueSky$Mountain#2025’ rather than simple passwords. These are easier to remember and significantly harder to crack.
Pros:
– It’s a simple method that comes with most file management systems
– Do not need internet to function
Cons:
– Weak passwords can be easily cracked.
– Does not track who accessed or modified the document
5. Secure cloud storage
Secure cloud storage, or cloud encryption, is different from on-premise encryption. Rather than storing data on local machines, companies can store them on encrypted cloud storage. This also offers automatic backups for extra security.
For even more protection, businesses often opt for zero-knowledge encryption. This ensures end-to-end encryption, meaning even the cloud service provider cannot access the stored data.
For example: Poka, a connected worker platform for manufacturers, needed a way to scan files for malware to meet SOC 2 compliance. Their in-house solution became slow and hard to maintain as file volume grew. They switched to a cloud-based solution that integrated seamlessly with their infrastructure, enabling real-time malware scanning and secure backup.
Pros:
– Prevents data loss due to hardware failure, accidental deletion, or cyberattacks
– Cloud providers offer advanced security measures
Cons:
– Documents cannot be accessed without the internet
– Choosing a trustworthy cloud provider requires a thorough review of security policies
6. Watermarking
Watermarking involves adding semi-transparent text, a logo, or an invisible code to a document as a mark of authenticity.
Invisible watermarks aren’t noticeable to the naked eye, while visible ones are placed over text to make copying difficult.
It is commonly employed when high-level security is not necessary but duplication of documents still has to be discouraged.
Pros:
– It deters the document copying and distribution
– Simple and straightforward to implement
Cons:
– Unauthorized viewing cannot be controlled by watermark
– If too aggressive, visible watermarks can obstruct viewing document content
7. Document tracking
Document tracking software helps monitor all activities related to a document’s circulation. These tools attach a tracking code to the document, logging every action taken, whether it’s being viewed, edited, or shared.
It can even capture details like who accessed it, their location, and what changes were made, while also notifying concerned parties in real-time.
Pros:
– Helps identify unauthorized access or insider threats
– Provides an audit trail and location tracking for compliance and investigations
Cons:
– Requires sophisticated tracking software
– Employees may feel overly monitored raising privacy concerns
8. Digital signatures
Digital signatures apply Public Key Infrastructure (PKI) to confirm the sender’s identity and prove the document’s originality.
A private key (held by the sender) is applied for encrypting the document that will be only decryptable using the public key (held by the recipient). A mismatch of keys results in non-decryption of the signature.
Pros:
– Prevents forgery and tampering as any modification invalidates the signature
– Legally recognized in many countries and admissible in court
Cons:
– Not applicable to physical documents.
– Non-tech-savvy individuals can find the setup process to be complex
E. Common mistakes to avoid in document security
1. Relying on a single security measure
Since all the documents require different levels of security based on their confidentiality, using the same method for all would not make sense.
For example, some documents would be fine with just a password but others might need layers of security like encryption + cloud storage.
2. Ignoring regular security audits
Without regular security audits, you might miss the signs of document vulnerabilities until the breach occurs. Hence it’s important to conduct timely audits to identify weaknesses and update security policies and protocols.
3. Failing to train employees
Human error is one of the biggest security risks, and untrained employees may unknowingly expose sensitive information through phishing and malware attacks.
However, internal document breaches can also be intentional, so you must be mindful of who you share sensitive information with.
Did you know? According to Verizon’s 2024 report, 35% of data breaches come from within organizations.
4. Not having a document breach response plan
Without a document breach response plan in place, an organization may suffer to react quickly to the breach.
Organizations must develop and regularly update an incident response plan to minimize the risk of any security incident.
F. Strengthen your document security with QR Mark
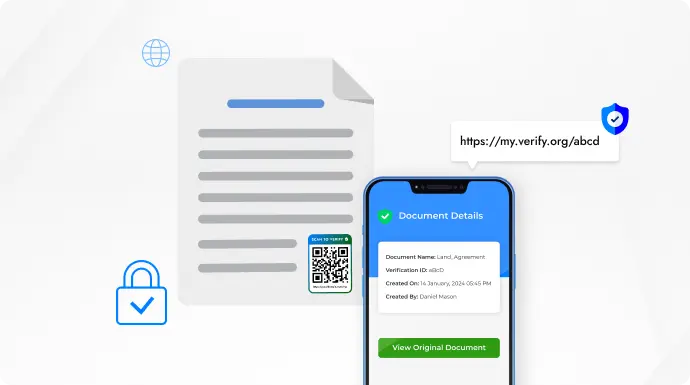
Verifying a document’s originality and integrity is just as important as protecting it from unauthorized access.
QR Mark simplifies this by allowing you to add a QR verification image to any uploaded document. This image contains a unique QR code with a verified domain for each document. You can adjust its size and placement as needed.
When scanned, the QR code directs users to a secure landing page displaying the original digital copy, along with key verification details like the creation date, owner name, document title, and a unique verification ID.
For added convenience, QR Mark integrates with popular document editing tools from Google and Microsoft Office. This way, you can add an extra layer of security and verification to your documents without disrupting your workflow.
G. FAQs
1. Is document security only a concern for large corporations?
No, file and document security is required for all companies, both large and small, and even for individuals who handle sensitive information.
Small enterprises also need to follow data protection policies and guard core documents like strategies, procedures, trademarks, and intellectual property. In reality, cybercriminals frequently prey on small firms because they lack strong security mechanisms.
It therefore becomes essential that all entities carry out appropriate security of records and documents.
2. How much does it cost to implement sufficient document security measures?
That depends on what level of security is needed. Simple security techniques such as watermarking, passwords, and access controls are no-cost or very low-cost but are not strongly secure.
Stronger verification measures such as QR code verification range from approximately $10 per month.
Full-fledged document management systems (DMS) for managing the life cycle of an entire document demand an investment in funds. Cloud-based DMS products range between $20 and $100 monthly, while on-premises solutions cost somewhere between $600 to $18,000 or more.
3. How do I determine what level of security a particular document needs?
Security level depends on the sensitivity and document’s sensitivity and potential impact if compromised. Consider asking yourself these questions:
– Is the document holding financially or personally identifiable information (PII)? Then it must be legally protected.
– Would unauthorized access incur legal or financial penalties? If so, tight security measures like encryption, access control, or QR validation are required.
– Is the document shared or accessed remotely frequently? If so, tracking and authentication measures are suitable.
4. How do I secure physical documents against counterfeiting?
To avoid counterfeiting, you can watermark, hologram, or apply specialty paper that contains security fibers. But both holograms and specialty paper are older technologies that can become expensive if you’re protecting a large volume of documents.
A better method is QR image verification, allowing you to instantly verify a document’s authenticity with no additional app for verification.
To summarize
Document security is not merely about preventing unauthorized access but also about guaranteeing authenticity, integrity, and compliance.
By integrating new solutions such as QR-based verification with robust policies and employee awareness, organizations can protect their documents effectively in both digital and physical formats.
Have questions? Comment below, and we’ll be happy to help!


Leave a Reply