Your files contain everything—work documents, contracts, personal records. But do you ever really think about their security?
One wrong click, a weak password, or a misplaced file, and your data could end up in the wrong hands.
But securing your files doesn’t have to be a hassle. In this guide, we’ll walk you through the meaning, practical methods, and best practices to protect your files. Let’s start!
A. What is file security?
File security refers to the practice of safeguarding files from vulnerabilities like unauthorized access, alteration, theft, and accidental loss.
It ensures that sensitive information remains safe on local devices, over the network, and even on the cloud servers.
File security, however, is not only a matter of passwords or the use of antivirus programs. It requires an active strategy based on three principles.
- Confidentiality: Makes it possible for only those authorized to view or alter a file. In other words, limiting who can view or modify a file to minimize the risk of unpermitted access.
- Integrity: Helps files stay in their genuine and original form except when altered by authorized personnel. Security features such as digital signatures, QR Codes, and watermarks do not allow unauthorized file modification.
- Availability: Helps files be available at all times. Regular backups, secure storage, and cyber security ensure you don’t lose vital information.
B. Why file security is more critical than ever in 2025

1. Evolving cyber attacks
Hackers no longer depend on brute force attacks or simple phishing emails. Some AI-powered malwares can now bypass traditional security measures. And ransomware (where attackers hold data hostage for money) targets not just businesses but also personal files.
A Gartner report predicts that by 2027, 40% of data breaches will stem from cross-border misuse of generative AI.
Even trusted platforms aren’t safe, attackers inject malware into software updates, compromising devices without users realizing it.
2. Remote work risks
With more people working from home or using personal devices for work, file security is no longer just an IT department’s concern.
Employees access sensitive data over public Wi-Fi, store files on unprotected devices, or leave their systems unattended in public. Without strong file protection, a lost laptop or an exposed file-sharing link could result in a major data leak.
3. Compliance with data protection laws
Organizations hold personal data worth billions of dollars, which can harm customers and businesses for violation of law when leaked.
Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) require companies to protect their documents. Failing to do so can lead to heavy penalties.
Did you know? Even a company like Meta (formerly Facebook) faced a €1.2 billion ($1.3 billion) fine by the Irish Data Protection Commission (DPC) for violating the GDPR guidelines. This largest GDPR fine ever was made because Meta continued to transfer European user data to the U.S. without adequate safeguards, violating privacy laws.
C. Practical methods to keep your files safe

1. Permission management
Not everyone needs access to every file. Permission management ensures that only the right people can view, edit, export, or share files.
The best approach here is Role-Based Access Control (RBAC), where users get access based on their job roles. For example, a finance team may have full access to budget files, while others can only view them.
Also, apply the principle of least privilege (PoLP). This includes giving users the minimum access necessary to do their jobs.
2. Use strong password protection
You can password-protect files on your cloud and desktop. Setting complex passwords is a simple yet effective way to protect files from brute-force attacks.
For added security, enable multi-factor authentication (MFA). This feature adds a second step (like a code sent to your phone) before granting access.
In 2024, statistics show that 30% of organizational data breaches result from employees reusing passwords or falling victim to phishing attacks.
3. Secure file-sharing
Sharing files the wrong way can let hackers intercept and manipulate data mid-transfer.
A case in point is that of Confidant Health, an online medical provider. In 2024, they accidentally leaked more than 120,000 files and 1.7 million activity logs because of an unsecured database.
To avoid these risks:
- Use Secure Transfer Methods – Rather than email attachments or unsecured links, use SFTP (Secure File Transfer Protocol) or FTPS (FTP Secure). These encrypt files in transit, making it much more difficult for hackers to intercept or alter them.
- Set Expiry Links – These automatically expire after a specified time. So, these don’t remain accessible longer than needed.
- Limit External Storage: Restrict personal USB sticks and external storage devices to prevent sensitive files from being copied and removed from secure systems.
4. File server auditing
File server auditing is the monitoring and logging of all file operations on a server, so that suspicious behavior is simple to identify.
- Track Activities – Auditing software documents every activity, including file access, edits, deletions, and changes to permissions. This assists in recognizing possible file security threats.
- Set Alerts for Suspicious Activity – Create alerts for unusual activities, such as recurring failed access or log-in attempts, and bulk file changes so you can act on time.
5. Verification with QR Codes
Maintaining a document’s integrity is essential to document security. QR Codes provide an easy method to authenticate this.
If a document contains a distinct QR Code, the recipients can scan it to authenticate its originality. The code directs to a secure, verified webpage managed by the owner, providing key information for verification.
It also refers to the original document, enabling cross-checking in real-time. This is particularly helpful in the case of contracts, reports, and certificates so that only the proper, unaltered version is utilized.
6. Secure cloud storage
Unlike local storage, where files are kept on a physical device, cloud storage allows data to be accessed from anywhere.
Hence, making it secure is even more important. Many businesses use SaaS platforms like Google Drive and OneDrive or iPaaS solutions to sync file transfers between different applications in one place.
Always choose a trusted cloud provider that offers end-to-end encryption. This ensures your data is protected both during transfer and while stored.
For example, services like Google Drive, Dropbox, and OneDrive offer encryption, but you should also enable two-factor authentication (2FA) to add an extra layer of security.
7. Encryption of sensitive files
Encryption converts plaintext into ciphertext format that can only be unlocked with a decryption key. This is especially important for sensitive files like financial records, contracts, or confidential business data.
For local storage, Encrypting File System (EFS) on Windows or FileVault on macOS can encrypt files automatically. For cloud storage, select service providers that use end-to-end encryption.
While sharing encrypted data, always save encryption keys externally, since in case an attacker obtains both of them, encryption is rendered meaningless.
8. Backup and recovery
Since availability is a key principle of file protection, having a backup and recovery plan is essential.
No file security is foolproof, but backups keep operations running after data loss, ransomware, or hardware failures. Cloud backups are automated, while local backups often require manual effort.
The best approach is the 3-2-1 backup strategy:
- Keep three copies of your data.
- Store them on two different types of media (e.g., local storage and an external drive).
- Keep one copy in an offsite or cloud backup to protect against physical damage or cyber threats.
D. Proactive strategies for long-term file security

1. Using VPNs
Companies use Virtual Private Networks (VPNs) to secure remote access to internal servers and databases.
A VPN encrypts internet connection, preventing hackers from intercepting sensitive data during file transfers or logins.
This is particularly important for remote employees and public Wi-Fi users.
2. Avoiding the illusion of security
Many businesses assume their documents are safe simply because they have passwords, firewalls, or antivirus programs. Security, however, is not about having measures in place, but rather about utilizing them properly and refining them constantly.
For instance, a good password is irrelevant if it’s used by employees on different platforms. An antivirus won’t help if systems aren’t updated regularly.
3. On-premise file security
On-premise file security starts with controlling physical access to storage devices and servers.
If unauthorized individuals can walk into a server room or access a hard drive, no amount of encryption can keep data safe.
Businesses should use biometric authentication, keycards, or PIN-based entry to restrict access. Surveillance cameras help monitor activity and detect security breaches in real time.
4. Incident response plan
An incident response plan is a set of instructions for responding to and recovering from security incidents.
It allows businesses to quickly contain the damage when an attack happens and return to normal business operations.
A good plan identifies clear roles and responsibilities so each team member has a clear next step.
5. Trained personnel
Having trained personnel is essential for maintaining file protection. Even in a small company, at least one specialist should oversee security protocols, detect threats, and respond to incidents.
However, security isn’t just an IT concern, human error remains one of the biggest risks.
Regular training on safe file handling, identifying cyber threats, and adhering to security policies helps minimize these risks and build a culture of accountability.
6. Keep software and systems updated
Keeping your software and systems updated is one of the easiest ways to strengthen file security.
Outdated programs have security gaps that hackers can exploit. That’s why updates and patches are released to fix these flaws and keep your files safe.
Ignoring them leaves your system open to attacks.
7. File storage analysis
File storage analysis means identifying and removing outdated, duplicate, or unnecessary files that may pose security risks.
Regular analysis ensures that sensitive data isn’t left in unprotected locations and that confidential files are properly classified.
Keeping storage organized and monitored not only helps find hidden security threats but also improves overall system efficiency.
E. Innovations in file security for better protection
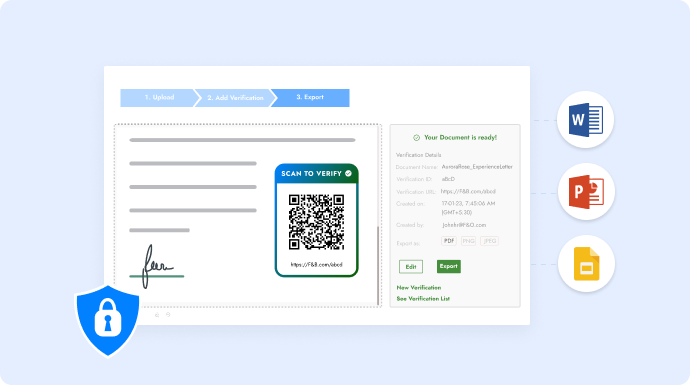
Traditional file security methods focus on restricting access, but ensuring document authenticity is just as important.
This is where QR Mark changes the game. It allows businesses to verify files instantly by attaching a secure, tamper-proof QR Code to each document.
When scanned, it leads to a verified source, confirming the file’s originality and preventing unauthorized alterations.
For example, Larynx, a translation agency, uses QR Mark on every translated document. With a quick mobile scan, no extra apps are needed.
Clients can instantly verify authenticity and ensure they receive only the original, unaltered file. This not only strengthens security but also builds trust, making document verification foolproof.
F. FAQs
1. How to secure files for free?
While advanced security software requires payment, there are still some handy free alternatives. You can encrypt files with built-in features such as Microsoft Office or zip file encryption.
For more protection, turn on encryption with BitLocker (Windows) or FileVault (Mac) to safeguard files even if your device gets accessed. Share files using cloud services such as Google Drive or OneDrive instead of risky ways.
Maintaining software up to date also prevents security threats. Also, QR Mark offers three free verifications per month, making it easy to check document authenticity.
2. Which security method is used to protect your files and the state of your computer?
Several security methods help protect both your files and your computer.
- Password protection: It is the first protective layer. Locking your device with a strong password and securing individual files with encryption ensures unauthorized users can’t access them.
- Antivirus software: It detects and removes malware that could corrupt or steal your files.
- Firewalls: These act as barriers, blocking harmful traffic from reaching your network.
3. What can be used to provide both file system security and database security?
File system security focuses on protecting individual files through permissions and encryption, while database security safeguards structured data within a database management system (DBMS).
To protect both:
- Encryption – For files, software such as BitLocker (Windows) and FileVault (Mac) encrypt stored documents. For databases, Transparent Data Encryption (TDE) keeps sensitive records safe even if accessed unauthorized.
- Access Control – Establish file permissions and apply Role-Based Access Control (RBAC) for databases.
- Backups – Save safe copies through cloud backups for files and automated database backups for databases.
- Network Security – Files are protected by firewalls and VPNs, whereas databases need Web Application Firewalls (WAFs) to prevent hacking attempts such as SQL injection.
- Monitoring – File systems record file activity, whereas databases employ audit logs to identify unauthorized modifications or abnormal queries.
In conclusion
Irrespective of the size, file security is non-negotiable for all businesses. You don’t have to employ all of these security measures at once, but it is essential to evaluate your risks and layer protection accordingly.
The most important thing however is to remain proactive, select the right security strategies, update them periodically, and never overlook the fundamentals.


Leave a Reply