With close to 90% of organizations expressing concern over document security, it’s no longer a question of ‘if’ but ‘when.’ Are your official documents truly safe?
In today’s hyper-connected workspaces, we share, store, and access documents at lightning speed. But while convenience has soared, so have the risks.
The truth is, most breaches don’t stem from sophisticated hacks but from everyday oversights.
TL;DR
- Official documents like contracts, certificates, and internal memos are prime targets for forgery, insider misuse, and accidental leaks.
- Physical documents aren’t immune: they can be stolen, faked, or damaged if not properly stored or tamper-proofed.
- Digital files need more than passwords; file-level encryption and strict access controls are non-negotiable.
- A few simple upgrades can prevent major reputational and legal damage down the line.
This blog digs into what document security really means, where the biggest risks lie, and how to protect what matters most.
A. What makes a document “Official”

An official document is any file that holds formal authority and is recognized as valid by an organization.
It could be used to verify identity, confirm decisions, or meet regulatory requirements.
These have three core characteristics: legitimacy, authority, and the legal or reputational consequences if they’re manipulated.
1. Common types of official documents
Here are some of the most common examples you’ll find across workplaces and institutions:
- Legal contracts – Define obligations between parties and are legally binding
- Government-issued IDs – Prove personal identity and citizenship
- Employee records – Contain sensitive HR data like salaries, evaluations, and disciplinary actions
- Internal memos – Document key decisions and communications within an organization
- Certificates – Academic, professional, or compliance-related credentials
- Reports – Financial, audit, or strategic reports that influence decisions and investments
2. Formats: Digital vs. Physical
Both digital and physical documents are vulnerable, but the risks differ.
- Digital documents are easy to alter without leaving obvious traces. Metadata can be erased, signatures replicated, and access shared discreetly. Without built-in verification, it’s simple to forge authenticity.
- Physical documents, though tangible, come with their own set of risks. They can be photocopied, swapped, or tampered with. Despite the rise of digital workflows, paper is still commonly used for contracts, IDs, and official records, making physical security just as important.
No format is inherently safer. Each has its unique vulnerabilities. And both require tailored protection strategies to defend against the specific risks they face. (Skip to Section C for strategies.)
B. Why Official Documents Are a Prime Target for Threats

Official documents are seen as trusted points of reference by people inside and outside your organization.
When someone sees a signed contract, a certificate, or an internal memo, they usually accept it as legitimate. That trust is exactly what makes these documents such high-value targets.
1. Forgery
This is when someone creates a fake document or alters a real one to serve their own agenda. This usually includes editing a legal agreement, faking a certificate, or duplicating a report with small changes.
The scary part? Forgery is often clean, subtle, and hard to notice. A single modified clause or date can completely change the outcome of a deal.
And with today’s tools, forgeries can look identical to originals.
What it leads to:
- Fraudulent transactions and unauthorized approvals
- Unqualified individuals passing off fake credentials
- Legal battles due to forged agreements
- Loss of trust in your brand or process
2. Insider misuse
In 2024, 83% of organizations reported insider-related security incidents. That tells you how common and dangerous this threat really is.
They come from people who already have access, like employees, vendors, or contractors. It might be intentional, like selling sensitive data for money.
Or careless, like editing the wrong version of a file. And because these individuals are supposed to have access, it’s harder to detect.
What it leads to:
- Loss of highly sensitive data can result in a competitive disadvantage
- Altered documents that misrepresent decisions or facts
- Damaged relationships with clients, partners, or regulators
- Legal exposure if misconduct isn’t caught and addressed
3. Unauthorized access
Not every breach starts with a hacker in a hoodie. Sometimes, it’s just a public folder link someone forgot to lock down. Or again, a former employee who still has access to internal files.
That’s unauthorized access, when someone gets into documents they shouldn’t. It happens more often than you’d think, especially when access controls are loose.
What it leads to:
- Leaked documents that weaken deal negotiations
- Stolen business plans giving competitors an edge
- Internal decisions exposed, risking backlash or lawsuits
- Violations of compliance laws (like GDPR, HIPAA, or PCI), resulting in penalties
4. Data leaks
Ever uploaded a file thinking it’s private, only to realize later it was public the whole time?
Or maybe you’ve seen a link passed around so much that anyone could open it. That’s how data leaks usually happen.
A data leak is when sensitive information gets exposed unintentionally without a breach or hack.
It often happens through unsecured cloud storage, misconfigured permissions, or overly broad sharing.
What it leads to:
- Confidential plans circulating outside the company
- Launch strategies or pricing leaks that ruin market advantage
- Private client or employee data exposed without warning
- Regulatory trouble if personal data wasn’t protected right
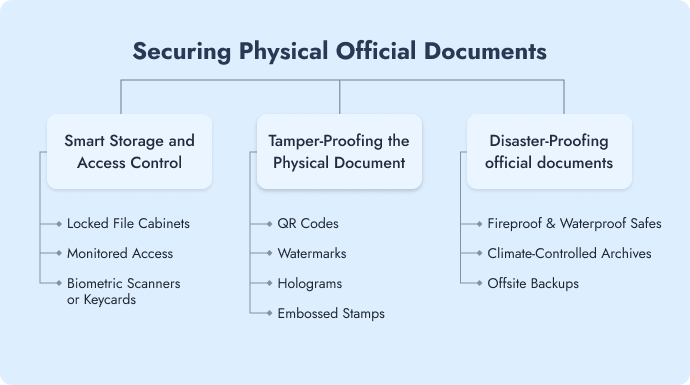
C. Securing physical official documents (The often-ignored risk)
In the digital age, physical documents don’t get the attention they deserve.
But walk into any office, and you’ll still see them as contracts, signed forms, IDs, certificates sitting in drawers or passed across desks. And that’s the thing: just because they’re offline doesn’t mean they’re secure.
Paper documents can be stolen, forged, lost in a fire, or even mishandled by someone who didn’t know better.
So, if your office documents live on paper, here’s how to actually protect them:
1. Smart storage and access control
The number one reason sensitive files get compromised is poor access control.
Securing your documents starts with knowing exactly who can get to them, when, and why. That’s the first line of defense for physical documents.
a. Locked file cabinets
Still essential for everyday protection. But don’t just lock them, make sure they’re in low-traffic zones, not out in the open.
And assign ownership. A locked cabinet is only as secure as the person holding the key.
b. Monitored access
Install CCTV or an access management system, track every person who accesses a document or enters a secure area. This alone deters casual snooping and insider mishandling.
c. Biometric scanners or keycards
For high-sensitivity areas (like legal archives or executive records), go beyond traditional locks.
Biometric systems (like fingerprint or iris scanners) or programmable keycards create individual-level access trails and revoke access instantly if needed.
Pro tip: Rotate physical keys and update digital access permissions quarterly. Many breaches happen simply because a former employee or contractor still has access.
2. Tamper-proofing the physical document
No matter how securely you lock them up, some documents eventually need to be shared. And you can’t exactly slap a password on a paper document to stop forgery.
But there are physical equivalents that work just as well when used right. These are built-in markers that prove authenticity and expose tampering attempts.
a. QR Codes
QR Codes on files are quickly becoming one of the smartest ways to secure physical documents. They can link to a verified online version, metadata, or a secure verification page.
The idea is simple: anyone who scans the code can instantly check if the document is real by landing on an official source with the original details.
Use it for Certificates, reports, or letters where digital verification adds a layer of trust.
b. Watermarks
A watermark is a faint, often hidden design embedded into the paper during production. It’s tough to replicate with basic printers or scanners. Hold it up to the light—it’s there, proving the document is real.
Use it for: Government papers, legal documents, anything where authenticity matters.
c. Holograms
These are the shiny, color-shifting seals you see on things like banknotes or official ID cards. They’re nearly impossible to duplicate without specialized equipment, making them a strong visual deterrent to forgers.
Use it for: Diplomas, licenses, or brand certificates that need next-level protection.
d. Embossed stamps
An embossed stamp raises the surface of the paper, creating a physical imprint that’s felt, not just seen. It can’t be photocopied or digitally recreated with accuracy.
Use it for: Notarized documents, official letters, or any document requiring authority.
3. Disaster-proofing official documents
Once your physical documents are protected from human threats, it’s time to consider environmental risks.
Fires, floods, humidity, or even just the passage of time can ruin valuable documents. The key here is to protect your documents from unexpected disasters that can cause irreversible damage.
a. Fireproof & waterproof safes
Fireproof and waterproof safes are your last line of defense in case of natural disasters.
Whether it’s a fire, flood, or even an accidental sprinkler mishap, these safes keep your physical documents safe. They’re essential for storing originals, signed contracts, or irreplaceable documents.
b. Climate-controlled archives
Ever pulled out an old document only to find it’s brittle or faded? Climate-controlled archives are designed to maintain consistent temperature and humidity levels, preventing the physical wear and tear that can happen over the years.
c. Offsite backups
Storing copies of crucial documents off-site protects you if disaster strikes at your primary location of organization. Think of it like cloud backup, but for paper documents.
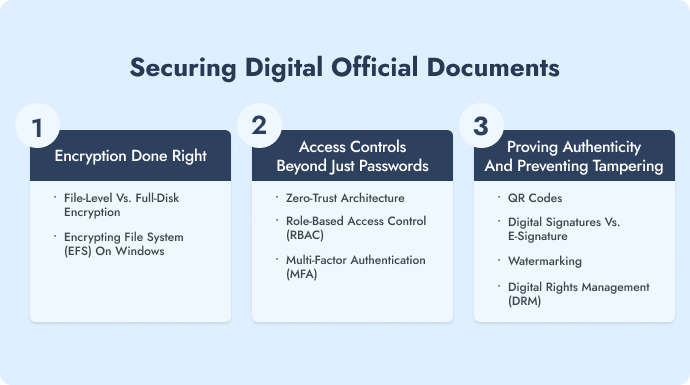
D. Securing digital official documents (Modern, yet vulnerable)
We’ve already covered how to protect documents in their physical form. But let’s face it, most of what we deal with today is digital. From contracts and certificates to internal records and reports, everything’s going online.
And while digital makes things faster and easier to manage, it also makes them easier to steal, sometimes without leaving a single trace.
That’s why digital document security isn’t just a nice-to-have anymore. It’s essential. So let’s look at how to do it right.
1. Encryption done right
a. File-level vs. full-disk encryption
Full-disk encryption (like BitLocker or FileVault) protects everything on a device, but only while it’s locked. Once someone logs in, the data becomes readable.
File-level encryption, on the other hand, secures individual documents, regardless of where they’re moved. If you’re sharing sensitive files or storing them in the cloud, this is a better choice.
b. Encrypting File System (EFS) on Windows
If you’re using Windows Pro or Enterprise, EFS is a built-in way to encrypt files or folders. Here’s how:
Right-click the file or folder > Properties > Click Advanced under the General tab > Check Encrypt contents to secure data > Hit OK
The file gets encrypted using your Windows user credentials. Just make sure you back up your encryption certificate because if you lose access, it’s all gone.
2. Access controls beyond just passwords
a. Zero-trust architecture
The old “trust but verify” model doesn’t cut it anymore. Zero-trust assumes no one is trusted by default, not even people inside your network.
Every user, device, and action needs continuous verification. It sounds heavy, but for sensitive environments, it’s essential.
b. Role-based access control (RBAC)
It lets you control who can access which documents based on their job role, not individually. On platforms like Google Workspace or Microsoft 365, this means setting up roles like owner, editor, commenter, or viewer for each file or folder.
The goal? Give people only the access they need to do their job and nothing more. So when someone joins, switches teams, or leaves, you can remove their access.
c. Multi-factor authentication (MFA)
It’s a pain for attackers and a safety net for you. Even if someone steals your password, they’ll still need your phone or biometric data.
Apps like Authy or Microsoft Authenticator make it easy to set up across platforms.
3. Proving authenticity and preventing tampering
a. QR Codes
Just like with physical documents, digital files can also carry QR Codes for verification. Tools like QR Mark give you a dashboard where you can generate and attach a QR Code to any document you issue.
When the recipient gets it, they can scan the code to see the verification details. The process works the same whether the document is printed or shared digitally.
b. Digital signatures vs. E-signatures
Most people confuse the two, but they’re not the same.
E-signatures are just an image of a signature or typed name on a document. Therefore, easy to copy.
Digital signatures, on the other hand, are cryptographic. They use a certificate-based key to “seal” the file. If anything in the document changes, even a space, the signature immediately breaks.
Note: Digital signatures do need a certificate from a trusted Certificate Authority (CA), but in most workplaces, this is handled for you.
c. Watermarking
Similar to how watermarks are used on physical documents, digital watermarking helps flag your files as official and discourages misuse.
You can start with visible watermarks like a company logo, “Confidential,” or the recipient’s name, layered right on the document.
These are great for instantly signaling that the file is sensitive or proprietary.
But that’s just the start. You can also add invisible watermarks, which embed tracking information that isn’t visible to the user but can still be used to trace leaks.
Then there are dynamic watermarks. These automatically pull in real-time details like the viewer’s name, email, or access time.
So, every person gets a uniquely marked copy. If it ever leaks, you’ll know exactly where it came from.
d. Digital rights management (DRM)
DRM gives you power over what happens to a document after you’ve shared it. It’s like putting a lock on the document’s actions, not just its access.
With DRM, you can stop people from printing, copying, forwarding, or even taking screenshots of the file.
You can also set expiration dates or revoke access at any time. So even if someone downloads the file, they can’t misuse it.
E. Transforming Official Document Security with QR Codes
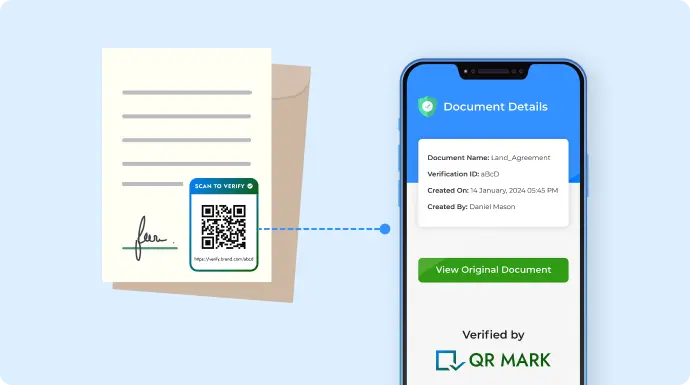
Document fraud is increasing at a rate of 20–40% over the last few years, and in many cases, it goes unnoticed until real damage is already done. In 2025, QR Codes have become one of the most reliable tools to secure official documents.
Take Soproni Larynx, a translation agency, for example. They use QR Mark to generate a QR Code on every document they translate, whether it’s an employee agreement, a training certificate, or even a doctor’s prescription.
So when the recipient gets the document, they can scan the code to instantly confirm that nothing was altered or forged along the way.
- Real-time verification – The moment someone scans the code, they can view the original, verified details.
- Cost-effectiveness – Compared to traditional verification systems, QR Codes are much lighter on resources but just as secure when implemented right.
-
Convenience – No logins or apps required. A simple scan is enough.
And it’s not just convenient for the end user, it’s equally simple to set up.
Here are the steps (we’ve used QR Mark here for its simple interface, but you can use any tool you prefer). QR Mark offers 3 free verifications per month, so you can try it out before deciding to scale.
1. Sign in or sign up on QR Mark.
2. In the dashboard, go to ‘Settings’ and add a custom domain. This is where your document verification pages will live.
3. Navigate to ‘Verifications’ and upload the PDF you want to secure.
Pro tip: Use add-ons for Google Workspace or Microsoft 365 to add QR Codes for verification as you create documents.
4. Select your custom domain instead of the default QR Mark domain.
5. Name your document and choose where you want the QR Code to appear. Just make sure the code is large enough to scan, but doesn’t cover key information.
6. Once done, click ‘Export PDF’ and your secured document is ready to go.
F. Best practices for sustainable document security in organizations

1. Know the legal & compliance landscape
Businesses today collect personal data like names, addresses, financial info, and even medical records. If this data isn’t protected, it can easily be misused, and the business could face heavy penalties.
That’s why it’s crucial to know what laws apply to you. GDPR, for example, regulates how personal data is collected and used, especially for EU customers. It emphasizes consent, transparency, and the right to be forgotten.
There are also industry-specific rules like HIPAA for healthcare data, GLBA for financial institutions, and PCI DSS if you handle credit card transactions.
2. Train your teams
Your security system is only as strong as its weakest human link. Most breaches happen due to simple oversights like sending the wrong file or using unsecured networks.
Start by educating your teams on what’s sensitive, what’s not, and how documents should be handled. Run mock drills for things like data leak response or phishing attempts.
And don’t just stop at onboarding, build in refreshers every few months. Security fatigue is real, and regular nudges help keep the guard up.
3. Create a security-first culture
Security should feel natural and not like extra work. It starts with leadership setting the example.
Make secure tools part of daily workflows so following best practices is easy, not optional.
And always recognize good behavior. When teams see that security is valued, they’re more likely to take it seriously.
4. Secure the entire document lifecycle
Most organizations secure the creation and storage part, but forget about what happens after. A document is vulnerable at every stage: from creation → sharing → editing → archiving → disposal.
When a file’s no longer needed, don’t just delete it. Shred paper documents and use certified or zero-trace tools to wipe digital ones clean.
FAQs
1. What’s the most effective way to secure official documents against tampering or forgery?
The most effective way to secure official documents is by using verification tools like QR Codes linked to an original digital version, digital signatures, or secure cloud storage with restricted access.
These methods strengthen official document security by allowing anyone to verify authenticity while preventing unauthorized changes.
2. How can I protect official documents that are shared in printed form?
To protect official documents in print, you can use tamper-evident features like watermarks, holograms, and QR Codes that link to a secure online version.
This ensures you’re securing sensitive documents even after printing, as the original data remains verifiable.
3. Are password-protected files enough to secure official documents digitally?
Password protection alone is not enough to secure official documents. It only prevents initial access.
For stronger official document security, use encryption, restricted permissions, and version control to prevent unauthorized access and modifications.
4. How can QR Codes help in securing sensitive documents?
QR Codes link physical or digital files to a secure verification source. When used properly, they provide a simple yet powerful way of securing sensitive documents, ensuring that recipients can confirm the document’s authenticity and integrity, essential for official document security.
5. What’s the best way for small teams to protect official documents without expensive tools?
Small teams can protect official documents by combining free or affordable tools, like encrypted cloud storage, access controls, and QR Code verification, to maintain strong official document security.
This is a cost-effective way to secure official documents and prevent misuse.
Moving forward
The risks tied to mishandled paperwork are real, so it’s important to take action before issues arise.
Whether it’s digital files or printed records, finding the right ways to secure official documents should never be an afterthought.
From smart access controls to tamper-proof features, even small steps can strengthen your approach to official document security. Stay consistent, stay aware.
Have a doubt or just wanna show some appreciation? Drop a comment below—we’d love to hear from you.


Leave a Reply