TL;DR:
Document fraud is rising fast, driven by digital tools and AI. To protect your business, use tamper-proof verification methods like QR codes, digital certificates, and watermarking; control document access; automate verification; and ensure full traceability.
Building a verification-first culture and aligning with compliance standards are key to stopping forgery, counterfeiting, and tampering in 2025.
If you’re worried about your documents being copied, edited, or misused, you’re in the right place.
Document security has never been more important. Whether it’s a fake certificate, a forged invoice, or a tampered licence, document fraud has become a serious threat to businesses and individuals alike.
Recent reports show that document fraud has gone up by almost 79% in the last few years. With remote work, online verification, and AI tools making forgery easier, anyone can create a fake document that looks completely real.
In this guide, we’ll break down how to stop document fraud using practical, proven methods that actually work. But first, let’s quickly look at what document fraud really means and how it’s changing in the digital era.
A. What Is Document Fraud?
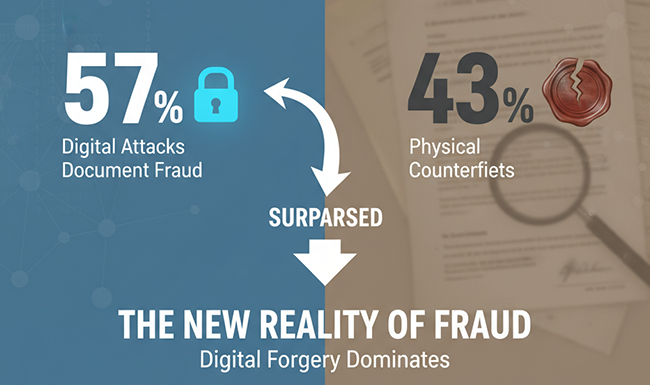
Document fraud refers to the creation, alteration, or misuse of documents with the intent to deceive or gain unauthorized benefits. In simple terms, it’s when a document is made to look genuine when it’s not.
Traditionally, document fraud meant forged signatures, counterfeit seals, or edited paper records. But as organizations moved online, the threat evolved.
Today, most document fraud happens in digital formats, through tampered PDFs, modified metadata, or synthetically generated content using AI.
There are two primary forms of intent behind it:
- Deliberate fraud: where documents are falsified for profit or advantage, such as fake degrees, licenses, or identity documents
- Opportunistic fraud: which occurs when someone slightly manipulates a document, like editing an invoice, changing a date, or reusing a certificate, to gain a smaller but still unethical edge
The consequences can be severe. Fraudulent documents can lead to financial loss, regulatory breaches, long-term reputational harm, and even legal action in regulated industries.
B. What Are the Different Types of Document Fraud?
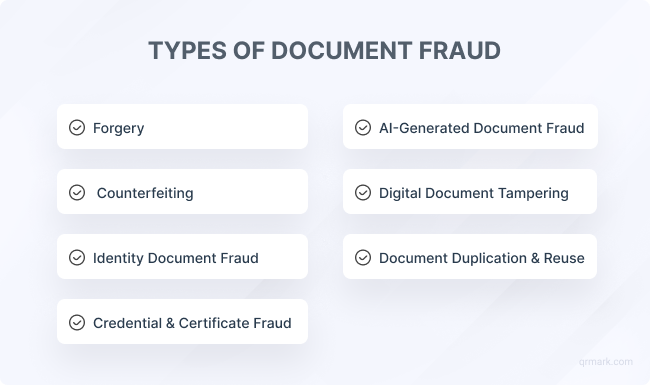
Some types of document fraud have been around for decades, others are new, powered by digital tools and AI. Here are the most common ones you should know about:
1. Forgery
This involves altering genuine documents to deceive others. It could mean changing text, modifying dates, replacing names, or forging signatures.
Even small edits to a PDF or scanned image can completely change a document’s meaning.
2. Counterfeiting
Counterfeiting is the creation of an entirely fake document designed to look official.
Examples include fabricated university degrees, business licenses, or identity cards made from scratch. These often use real logos, templates, and fonts to appear legitimate.
3. Identity Document Fraud
This type targets personal identification, like passports, national IDs, or driver’s licenses.
Fraudsters use stolen information or fake credentials to impersonate someone else or create a new, synthetic identity.
4. Credential and Certificate Fraud
Fake academic or professional credentials are becoming more common, especially with remote hiring and online learning.
Fraudsters often rely on diploma mills, which are unaccredited institutions that sell fake degrees or certificates.
These documents look convincing and can easily mislead employers or verification teams if proper checks for certificate verification aren’t in place.
5. Digital Document Tampering
Modern tools make it easy to manipulate PDFs, metadata, or digital signatures.
Fraudsters can alter timestamps, approval details, or embedded verification data without leaving visible traces, making this one of the hardest forms to detect manually.
6. AI-Generated Document Fraud
AI tools can now produce realistic fake documents, complete with synthetic signatures, fabricated layouts, and generated names or seals.
According to Sumsub’s Q1 2025 Identity Fraud Report, deepfake fraud rose by 1100%, while synthetic identity document fraud increased by over 300% in the U.S. This shows how quickly attackers are using AI to generate fake credentials and biometric data.
These AI-made forgeries often pass basic visual checks, making real-time digital verification the only reliable way to confirm authenticity.
7. Document Duplication and Reuse
Here, an authentic document is reused multiple times for fraudulent purposes. For instance, someone might reissue a legitimate invoice or certificate under different names to gain benefits multiple times.
C. How to Stop Document Fraud in 2025
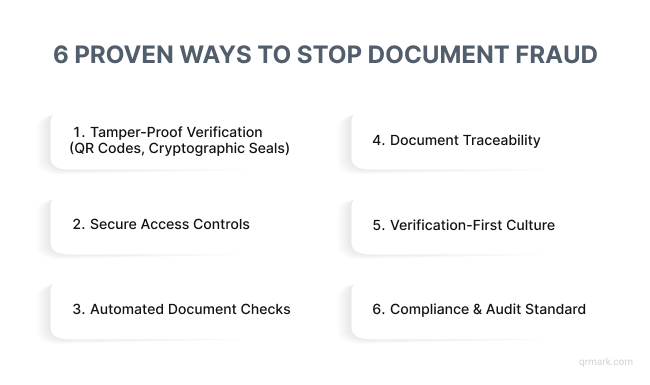
Let’s look at the most effective methods that organizations are using right now to keep their documents secure.
1. Use Tamper-Proof Verification Technologies
a. QR Codes for Verification
QR Codes are quickly becoming one of the most effective ways to protect both digital and physical documents.
Each document gets a unique QR Code linked to a secure record that verifies its authenticity, issuer, and metadata in real time. This makes it almost impossible for anyone to forge or reuse the same document undetected.
Many organizations now use QR Mark, a trusted leader in this space, because it lets them host verification on their own domain, for example, verify.yourcompany.com. This builds trust and keeps control in their hands.
Institutions like the Auburn Institute of Maritime Training use QR Mark to add QR Codes to their certificates, ensuring instant verification and full compliance with regulatory standards.
b. Digital Certificates and Cryptographic Seals
Digital certificates use cryptographic keys (like X.509 protocols) to prove authenticity.
When a document is signed with a verified certificate, anyone can check its legitimacy through a trusted certificate authority (CA). This ensures the document hasn’t been changed since it was issued.
c. Watermarking and Invisible Digital Fingerprints
Digital watermarks or hidden fingerprints can be embedded directly into document files.
These identifiers aren’t visible, but can confirm whether a document is original or has been copied or edited. It’s an extra layer of protection that helps trace misuse even after a document has been shared.
2. Implement Secure Issuance and Access Controls
Most document fraud starts with weak access management. Limit who can issue, edit, or approve sensitive files.
Use role-based access control so only authorized personnel can handle official documents. Combine that with multi-factor authentication (MFA) for added security.
Every document should also be encrypted end-to-end, both in storage and during sharing. If you’re integrating external verification systems, make sure you’re using secure APIs and tokens to prevent unauthorized access or manipulation.
3. Automate Document Verification
Manual checks can’t keep up with modern fraud tactics. AI-based verification tools can spot tampering that humans miss.
They analyze document structure, layout, and metadata to flag inconsistencies. For example, an AI tool can detect if a signature was pasted in or if a date stamp doesn’t match the file history.
These systems can also compare documents against verified templates or external databases in real time.
Integrating automation into key workflows, such as HR onboarding, vendor screening, or credential verification, saves time while reducing human error.
4. Ensure Document Traceability and Lifecycle Management
Every document should have a digital footprint. Assign each one a unique identifier, like a QR Code, blockchain hash, or tracking number, to maintain full traceability.
Keep digital logs of every action: when it was issued, viewed, shared, or verified. This creates a transparent audit trail that discourages manipulation and makes it easier to detect unusual activity.
Version history tracking is equally important. It ensures that legitimate updates are recorded while preventing unauthorized edits.
5. Build a Verification-First Culture
Even the best technology fails if people don’t use it. Make verification part of your organization’s culture.
Train employees, vendors, and clients to verify before trusting any document. Always include verification links or QR instructions directly on official documents so it’s easy to check authenticity.
Internally, create clear policies that require verification for any external or third-party document. The more people adopt this mindset, the harder it becomes for fraud to slip through.
6. Align with Compliance and Regulatory Standards
Finally, make sure your fraud prevention framework aligns with major compliance standards. Follow KYC (Know Your Customer) and AML (Anti-Money Laundering) requirements if you handle identity or financial documents.
Implement ISO 27001 or similar information security standards to ensure your document systems meet international benchmarks.
Regular audits are key. They help identify weak points and ensure your security and verification tools are performing as intended.
D. How QR Mark Helps Prevent Document Fraud
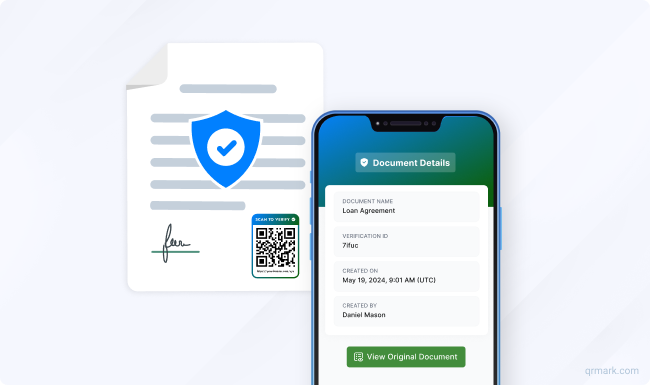
QR Mark makes document verification easy. It adds a secure QR Code to each document, which links directly to a trusted verification page. When scanned, it instantly confirms if the document is genuine.
It’s affordable, simple to use, and gives you full control by letting you verify documents under your own domain, so your brand stays front and center.
Here’s how to get started:
-
Go to qrmark.com and create an account or log in.
- Open settings and add your custom domain (for example, verify.yourcompany.com) to link documents to your brand.
- Go to verification, and click on create verification, then upload the file you want to secure.
Tip: Use the Bulk Upload feature to secure up to 20 documents at once if they follow a similar format.
- Select your custom domain, choose a landing page template (if you’ve made one), and name your document.
- Pick whether to place the QR Code on all pages or a specific page.
- Click generate verification image, adjust the placement if needed, and then download.
Your document is now secured with QR Mark.
You can also use QR Mark’s add-ons for Google Workspace and Microsoft Office to secure files as you create them, right inside your usual workflow.
E. Who Should Be Most Protective Against Document Fraud
1. Educational Institutions
Should secure: Degrees, transcripts, training certificates, and admission letters.
Fake certificates and transcripts can harm your institution’s credibility. Verified digital documents protect your reputation and make it easier for employers and regulators to trust your credentials.
2. Government and Legal Bodies
Should secure: IDs, permits, licenses, public notices, and legal certificates.
Forged permits or IDs can enable serious fraud and security risks. Real-time verification helps maintain public trust and ensures only authentic documents are in circulation.
3. CPG (Consumer Packaged Goods) Companies
Should secure: Contracts, invoices, vendor documents, warranty cards, product certifications, and certificates of authenticity.
Fake supplier documents or counterfeit certificates of authenticity can lead to recalls, compliance issues, and a loss of consumer trust.
Securing these records with real-time verification helps keep your supply chain transparent and your brand protected.
4. Healthcare Organizations
Should secure: Medical records, prescriptions, insurance forms, and patient reports.
Even small document changes can lead to false claims or endanger patient safety. Securing these records supports HIPAA (Health Insurance Portability and Accountability Act) compliance and helps maintain data integrity.
5. Food and Safety Compliance Authorities
Should secure: Inspection reports, safety certificates, and regulatory approvals.
Tampered compliance certificates can expose consumers to unsafe products. Verified documentation helps meet food safety standards like HACCP and ISO 22000 while keeping every record traceable.
6. HR and Recruitment Teams
Should secure: Reference letters, salary slips, offer letters, and employee records.
HR teams handle sensitive documents that directly represent the company. If these are tampered with, it can lead to fake employment claims, payroll manipulation, or data breaches.
Securing all HR documents with verified issuance protects the company’s integrity and prevents misuse.
7. Financial Institutions and Insurance Providers
Should secure: Loan documents, policy forms, KYC records, and claim approvals.
Document manipulation in finance or insurance can directly lead to monetary loss and compliance breaches. Verified digital records keep transactions transparent and auditable.
8. Real Estate Companies
Should secure: Ownership records, title deeds, lease agreements, and compliance approvals.
Property fraud often starts with forged paperwork. Securing these documents supports real estate due diligence and regulatory compliance, protecting both clients and the firm’s reputation.
F. How to Respond If You Suspect Document Fraud
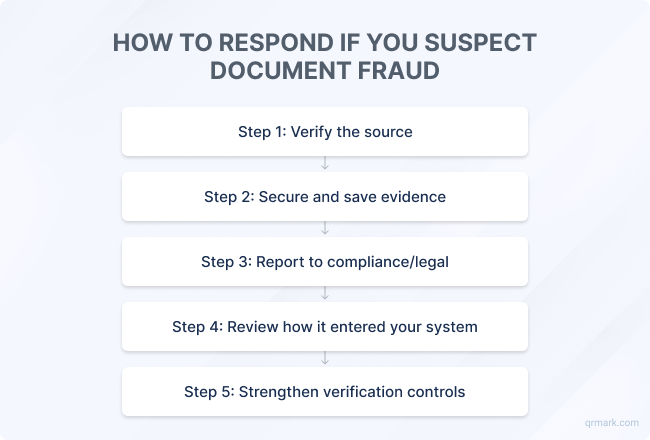
If you ever come across a document that doesn’t seem right, whether it’s a mismatched signature, an altered PDF, or an unverifiable certificate, don’t rush to delete or confront.
How you respond in the first few steps makes all the difference.
1. Verify the Source
Start by checking where the document came from. Scan the verification code if it has one or contact the issuing organization directly.
Always verify through official channels, not links or email addresses in the document itself.
2. Isolate and Secure Evidence
Save the document in its current state and store it securely. Keep all related emails, attachments, and metadata.
Avoid making edits or conversions that might overwrite timestamps or digital trails.
3. Report the Incident
Inform your internal compliance or legal team immediately. If you’re part of a regulated industry like finance or healthcare, report it under your organization’s fraud response protocol or to the relevant authority.
4. Review Internal Processes
Once confirmed, trace how the fraudulent document entered your system. Was it uploaded by a vendor? Sent through email? Shared by an employee? This helps identify process gaps that need tightening.
5. Strengthen Your Controls
Use the incident as a trigger to improve verification systems. Introduce or enforce document validation tools like QR-based verification, access controls, or automated checks.
Also, train your teams to recognize signs of tampering early on.
G. FAQs

1. How can document forgery be prevented?
Document forgery can be prevented by combining secure issuance processes with tamper-proof verification tools.
Each official document should include a unique QR Code or cryptographic signature that links back to a trusted source for real-time verification.
Organizations should also restrict who can issue or edit documents using role-based access controls and multi-factor authentication.
Adding digital watermarks or invisible identifiers inside documents further prevents forgery and helps trace misuse.
2. How do I stop someone from misusing a photocopy of my document?
To prevent misuse of photocopies, mark all physical copies with visible text like “COPY” or “NOT VALID FOR OFFICIAL USE.”
You can also include a QR verification link on the original version. That way, even if someone duplicates it, the verification system will instantly show whether the document is genuine or just a photocopy.
If you’re issuing sensitive certificates or approvals, make sure only digitally verifiable originals are accepted as valid proof.
3. Can QR Codes really prevent document fraud?
Yes. QR Codes are one of the simplest and most effective anti-fraud technologies available.
When each document has a unique QR Code linked to a secure verification record, it becomes nearly impossible to forge or reuse it undetected.
Anyone can scan the code and instantly confirm details like issue date, issuer name, and authenticity, removing the need for manual verification or guesswork.
4. What are the common signs that a document might be fake?
A document may be fraudulent if you notice:
- Unusual fonts, spacing, or layout differences.
- Low-quality or pixelated seals and logos.
- Missing or invalid verification codes.
- Metadata showing different authors or creation dates.
- Contact details that don’t match the real issuer.
5. Can small businesses protect documents without expensive systems?
Yes. Small businesses can implement affordable security measures like QR Mark, password-protected PDFs, and digital signatures.
Even simple practices like restricting document editing rights, using encrypted cloud storage, and training staff to verify documents before approval can drastically reduce the risk of fraud.
Final Thoughts
Document fraud isn’t a problem that disappears overnight. It keeps adapting as technology changes. But the way we protect our documents can adapt too.
Simple steps like adding verification, tracking access, and training people to check authenticity make a huge difference.
If you’re just starting to secure your documents, tools like QR Mark make it easier to take that first step. It lets you test real-time verification without a big commitment; you even get three free verifications each month to try it out.
The goal isn’t to add more complexity to your process. It’s to build confidence that every document you share or receive is genuine, and that’s something every organization can benefit from.


Leave a Reply