Physical documents are still highly relevant, especially for official purposes. One reason is that they are generally harder to forge than digital copies.
But does that mean they’re free from risks? Not at all. Physical documents come with their own security challenges.
Think about it—a confidential contract left on a desk, a signed agreement tossed in the trash, or a sensitive file accessed by someone who shouldn’t have clearance. These everyday mistakes can lead to serious consequences.
In this blog, we’ll dive into the challenges of physical document security, explore ways to protect them and go over the dos and don’ts.
Let’s begin.
A. Understanding the risks to physical document security

1. Unauthorized access
Unauthorized access to physical documents happens when someone without proper permission gets hold of them. It is usually due to poor access controls or careless handling of documents.
Once in the wrong hands, these documents can be photocopied, photographed, edited, or even destroyed, without anyone knowing.
In contrast to digital files that create access logs, it is impossible to trace who has opened or manipulated a physical document without having strict security protocols in place.
2. Theft and espionage
Theft and espionage typically hit valuable documents such as contracts, financial reports, and intellectual property. These documents may be stolen to secure a competitive advantage or sold in the black market.
Did you know? In Q3 2024 alone, data breaches exposed over 422 million records, underscoring the rising threat of information theft.
A single incident can have severe implications causing financial loss, regulatory fines, and long-term reputational damage to a business.
Protecting sensitive documents from theft is not merely about security but protecting business integrity.
3. Environmental damage
Unlike digital documents, physical documents are highly vulnerable to natural disasters like fire, floods, and tornadoes, which can wipe out entire archives with no chance of recovery.
But it’s not just large-scale disasters, poor storage conditions can also cause damage over time. Humidity, pests, and mold can slowly degrade documents, making them unreadable when they’re needed.
4. Human errors
Human errors are among the major causes of document handling security breaches.
Employees leave files exposed, send confidential documents to an inappropriate recipient, leave them without supervision, or lose important documents, resulting in unintended disclosure.
5. Insider threats
Unintentional exposure of sensitive data is not always an error but is deliberate at times. This comprises employees, contractors, or business partners who abuse their privilege to physical documents for financial advantage or malicious purposes.
Insider risks are more difficult to detect since they are from trusted personnel with legitimate access and can lead to much greater loss.
Did you know? 95% of data breaches include human mistakes such as insider threats and misuse of credentials, according to Mimecast’s State of Human Risk Report 2025.
6. Lack of disposal protocols
Inadequate disposal such as simply discarding documents keeps it open to the possibility of it still being accessed and exploited.
“Dumpster diving” is a serious security threat, where attackers extract sensitive data from trash containers or recycling facilities. Even shredded or torn documents can at times be reassembled if not disposed of appropriately.
B. Practical methods for physical document security

1. Secure storage solutions
Sensitive documents should be stored in cabinets or safes equipped with high-security locks, such as keyless electronic locks or biometric access.
These measures prevent unauthorized handling and reduce the risk of theft.
a. Lockable filing cabinets and safes
Important documents should be stored in cabinets or safes with high-security locks (e.g., keyless electronic locks or biometric access). These help prevent unauthorized handling while also protecting against theft.
b. Restricted-access document storage rooms
Organizations handling classified or sensitive data should have designated storage rooms with controlled access.
Entry should be limited to authorized personnel through badge systems, biometric scans, or secure keycard access.
c. Access logs & monitoring
Keeping track of who accesses documents and when they do so helps ensure accountability. Access logs and surveillance systems can detect potential security breaches before they escalate.
d. Fireproof and waterproof storage solutions
Environmental threats like fires and water damage can permanently destroy documents.
Investing in fire-resistant safes, waterproof document holders, and climate-controlled storage helps safeguard critical records from unforeseen disasters.
2. Digital verification for physical documents
How do you verify whether a physical document is original or tampered with? Forgery doesn’t always involve stolen or misplaced documents.
Many industries, including healthcare, finance, government, education, retail, and insurance, face issues where people alter original documents or use fakes for fraudulent purposes.
A simple yet effective solution is attaching a QR Code to every document your company issues. Unlike static seals or holograms, QR codes link to an encrypted digital record, making unauthorized duplication or forgery nearly impossible.
Even if someone gains access to your physical document, they can’t generate a valid QR verification code that links to your company’s secure verification page.
Example: Larynx, a translation agency, ensures document authenticity by using QR Mark on every translated document, whether from Hungarian to German or English.
3. Document tracking and management
Keeping track of hard copies of documents is just as important as securing them. Without a system to monitor document movement, the risk of misplacement, theft, or unauthorized duplication increases.
a. Maintaining a document inventory system
Businesses should keep a real-time catalog of all physical documents, detailing location, handler, and last accessed time to prevent accidental loss.
b. Using RFID tags
RFID (Radio Frequency Identification) tags can be installed on sensitive documents and RFID readers are placed at entry points, cabinets, or storage areas. This automatically logs document movements when passing RFID readers, triggering alerts if removed from a designated area.
4. Secure document handling and transport
Physical document security is at its most vulnerable when being moved or accessed. Secure handling prevents interception or misplacement.
a. Sealed containers
Confidential files should only be transported in tamper-proof containers or locked briefcases. For example, The CIA uses tamper-evident bags, also known as burn bags, to transport classified documents securely.
b. Secure courier services
When sending documents externally, use vetted courier services that provide tracking and proof of delivery.
c. Controlled printing & copying
Only authorized personnel should be allowed to print or duplicate sensitive documents. Networked printers should have security logs to track usage.
5. Document disposal and destruction
Not every document needs to be stored forever. Holding onto outdated records not only increases the risk of unauthorized access but also adds unnecessary storage costs and clutter. Proper disposal ensures that sensitive information doesn’t fall into the wrong hands.
Here are the two most effective methods for secure document destruction:
a. Cross-cut shredding
Unlike basic strip-cut shredders, cross-cut shredders slice documents into tiny, unreadable particles, making reconstruction virtually impossible.
b. Incineration & pulping
For highly sensitive documents, incineration or pulping (turning paper into a liquid pulp) ensures complete destruction, leaving no chance of recovery.
Did you know? The U.S. Department of Energy permits the use of incineration for destroying classified matter, ensuring complete elimination with no possibility of reconstruction.
C. Common mistakes to avoid in physical document security

1. Relying solely on locks without monitoring
Most companies think that it is sufficient to lock cabinets, safes, or storage rooms in order to secure the documents.
Physical locks can be picked, keys can be duplicated, and intruder access can be made undetected if there is no surveillance.
Without surveillance cameras or access logs, there’s no way to track who has viewed or removed a document.
2. Failing to regularly update security protocols
Security threats keep on evolving, yet many organizations focus on cyber risks while neglecting physical document security.
Outdated methods like sealed envelopes, holograms, locks, or specialized paper may still be costly but may not be completely secure against today’s threats.
In order to be one step ahead, companies need to constantly evaluate threats and revise their security protocols to keep documents secure from evolving dangers.
3. Overlooking unattended documents
Leaving sensitive documents on desks, in printers, or in meeting rooms is a common but serious mistake.
Office printers also store copies of printed and scanned files on internal hard drives, which can be exploited if not cleaned regularly.
Enforcing a clean desk policy, where employees store documents securely before leaving their workspace, and regularly wiping printer storage can help prevent data leaks.
4. Assuming a single security measure is enough
Many organizations rely on just one security measure, such as locked cabinets or surveillance cameras, without realizing that a layered approach is necessary.
A lock may protect documents from casual access but won’t prevent unauthorized copying, while surveillance cameras can record theft but won’t stop it.
A strong physical document security strategy should combine multiple measures like restricted access, tracking systems, QR-based verification, and secure disposal methods, to ensure 360-degree protection.
5. Failing to train employees on physical document security
Strict security measures can be put in place, but it’s still the employees who must enforce them. Human mistake is still one of the greatest weaknesses in physical document security.
Without training, employees can mess up sensitive documents or not recognize social engineering attempts such as impersonation.
Regular security training, clear guidelines, and periodic refresher courses can help reduce mistakes and ensure employees are accountable for maintaining document security.
6. Not having a contingency plan for lost or stolen documents
Document loss or theft can happen to any organization, yet many lack a clear response plan. Delays in action can lead to increased financial damage or halt operations.
Digital backups help recover lost documents quickly, while QR-based verification prevents unauthorized duplication or forgery.
D. A Smarter approach to protecting physical documents
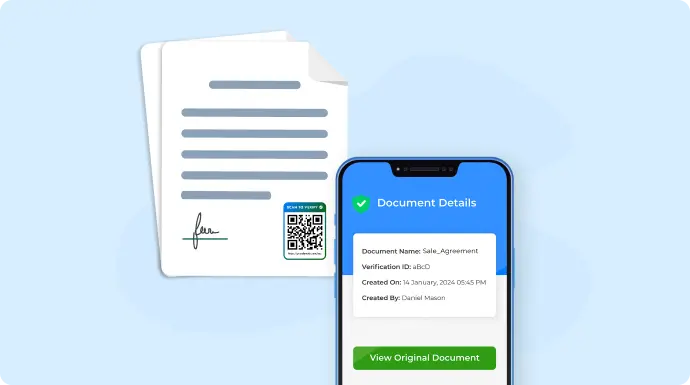
Traditional security measures have limits. Once a document leaves your hands, how do you ensure it isn’t misused?
This is where modern verification methods step in. QR Mark secures documents by adding a unique QR Code to each one. When scanned, it takes you to a secure page showing key details like the document name, owner, creation date, and unique ID.
The best part? Anyone can scan it to verify authenticity—no special app or login is needed. These QR Codes can’t be faked because they’re tied to a verified domain. They can only be created through authorized access to a secured dashboard. If there’s ever doubt, the original digital copy is always available for verification.
This way, by combining hard copies of documents with digital verification you can ensure your documents remain authentic.
E. FAQs
1. What is physical document security?
A physical document is an actual record in the form of paper, e.g., contracts, reports, or certificates. Physical document security is the process of safeguarding these documents from illegal use, theft, tampering, destruction, or loss.
2. Why is physical document security important?
Sensitive files hold vital data that, once leaked or compromised, can generate financial loss, identity theft, or legal issues. Numerous businesses are also obligated to abide by legal laws such as GDPR, HIPAA, and ISO policies, which charge organizations with maintaining confidential records securely. Physical record protection failure results in data exposure, legal penalties, and damages to reputation.
3. What is the best practice for handling sensitive physical documents?
The best practice for handling sensitive physical documents is a layered approach that combines secure storage, controlled access, monitoring, and proper disposal. Furthermore, employing scannable verification techniques, including QR Codes, enables instant authentication, preventing forgery and guaranteeing document authenticity.
4. How do you secure physical documents?
Physical documents need to be secured with multiple layers of protection:
- Safe storage in fire-resistant, locked cabinets.
- Access control by badge entry or biometric recognition.
- Monitoring and surveillance with CCTV cameras and alarm systems.
- Document verification with QR Codes to verify documents and identify tampering.
- Secure disposal by shredding, pulping, or incineration.
The Bottom Line
Physical document security isn’t just about keeping papers locked away—it’s about staying ahead of risks.
Theft, forgery, and mishandling can happen anytime, but a proactive approach ensures your documents remain safe and verifiable. Secure storage, controlled access, and modern verification methods work together to prevent misuse.
Ignoring document security isn’t an option. What are your thoughts? Drop your questions or insights in the comments below!


Leave a Reply