TL;DR
• Document security solutions are software tools that protect your digital and physical documents from unauthorized access, leaks, and cyber threats.
• They include encryption software, QR code verification, access controls and permissions, Digital Rights Management (DRM), audit trails, secure cloud storage, watermarking, and digital signatures.
Did you know that over 50% of businesses experienced at least one cyberattack in 2024? And here’s the kicker – document breaches alone cost companies an average of $4.45 million per incident.
If you’re reading this, you’re probably worried about keeping your business documents safe. Maybe you’ve heard horror stories about data leaks. Or perhaps you’re just trying to figure out which document security solutions actually work without breaking the bank.
Good news: Protecting your documents doesn’t have to be complicated. Let me walk you through everything you need to know about document security in 2025.
A. What are document security solutions and why do you need them?

Think of document security solutions as a digital vault for your business files. They’re software tools that protect your digital and physical documents from prying eyes, accidental leaks, and cyber threats.
In simple terms, it’s how you keep control over your data. Whether you’re sending a client proposal or storing sensitive contracts, document security makes sure only the right eyes see the right information.
Here’s why you should care about document security
1. Keeps your data private
Not every file should be visible to everyone. Critical document security solutions ensure that sensitive information, such as client data, financial records, or intellectual property, remains protected and is only accessible to those who need it.
2. Protects your business reputation
A single leaked document can destroy years of trust. Clients, investors, and partners expect you to handle their data with care. Solid security shows them you take that seriously.
3. Supports compliance
Whether you’re dealing with GDPR (for handling EU citizens’ data), HIPAA (for patient health records), or ISO standards (for general info security), document security helps you stay legally compliant and avoid hefty fines.
4. Prevents fraud
With tools like QR code verification and digital signatures, you can stop forged or tampered documents from slipping through. What you send is exactly what they receive, no edits and no fakes.
5. Provides peace of mind
When your documents are secure, you don’t have to constantly worry about who might be snooping or leaking. That mental load is off your plate, and you can focus on running your business.
6. Reduces human error
Let’s be honest, mistakes happen. But with automated access controls, encryption, and audit trails in place, even when someone slips up, the system catches it before it turns into a crisis.
B. Top 7 document security solutions every business needs

Let me break down the essential document security solutions that actually make a difference:
1. Document encryption software
Encryption scrambles your documents into unreadable code. Only people with the correct decryption key or password can unlock and read the contents.
Think of it like this: if someone hacks into your system and grabs an encrypted file, all they get is digital gibberish. Totally useless to them. That’s why encryption is considered your first and strongest line of defense.
Popular tools: AxCrypt offers simple file encryption, perfect for small businesses. For enterprises needing more muscle, Symantec Endpoint Encryption handles everything from individual files to entire hard drives.
2. QR Code document verification
Here’s where things get interesting. QR code verification adds a physical-digital bridge to document security. Each document gets a unique QR code that proves it’s authentic.
Scan the code, and you instantly know if the document is real or fake. It’s like giving each document its own unforgeable ID card.
This works through either blockchain or a custom domain system. Blockchain is secure, but custom domain-based verification gives you more control and a fully branded experience, making it the go-to for most businesses today.
Popular tool: QR Mark leads the way with custom domain-based document verification. It’s fast, secure, and gives your files a level of credibility that’s hard to fake.
3. Document access control and permissions
Access control decides who sees what. It’s like having a bouncer for each document.
Modern access control systems are smart. They consider who’s asking, when they’re asking, and where they’re asking from. Your CFO might access financial documents from the office but get blocked from a coffee shop.
Leading solutions: Microsoft Information Protection integrates seamlessly with Office 365. For more advanced needs, Varonis offers incredibly detailed permission management that tracks every file interaction.
4. Digital rights management (DRM)
DRM goes beyond basic access control. It controls what people do with documents after opening them.
Want someone to read a document but not print it? DRM handles that. Need to stop screenshots? DRM again. It even works after someone downloads the file.
Top platforms: Adobe Experience Manager excels at DRM for PDFs and creative files. For general business documents, Vitrium Security provides flexible DRM that works with any file type.
5. Comprehensive audit trails
Audit trails record everything. Who opened what, when they opened it, and what they did with it. It’s like having security cameras for your documents.
This isn’t just about catching bad actors. Audit trails prove compliance, settle disputes, and help you understand how your team uses documents.
Best options: Netwrix Auditor specializes in detailed document tracking across multiple platforms. For simpler needs, most cloud document security platforms include basic audit trails.
6. Secure cloud storage
Cloud storage lets you save documents online so you can access them from anywhere, on any device. But not all cloud platforms are built for security.
Secure cloud storage encrypts files before upload, during transfer, and while stored. The best platforms add extras like automatic backups and geographic redundancy.
Trusted providers: Tresorit offers zero-knowledge encryption – even they can’t read your files. For businesses already using Microsoft, OneDrive for Business provides solid security with a familiar interface.
7. Document watermarking
This isn’t the old-school “Confidential” text behind a page. It’s smarter and way more secure.
Traditional watermarks are just static. You add them once, and they look the same on every copy. But in document security, watermarking is dynamic. That means the watermark changes depending on who’s viewing the document.
Let’s say you share a draft contract with three people. Each version gets its own watermark showing the viewer’s name, email, IP address, and time of access. If one of those versions leaks? You instantly know where it came from.
Effective tools: FileOpen offers dynamic watermarking that changes based on who’s viewing. For simpler needs, most document editors include basic watermarking features like MS Word or Google Docs.
8. Digital signatures
A digital signature is an electronic way to sign a document and prove it hasn’t been changed after signing.
It’s more than just typing your name. Each digital signature is tied to a certificate issued by a trusted Certificate Authority (CA) and includes a timestamp. That makes it tamper-proof and legally valid in most countries.
Popular platforms: DocuSign is the easiest to use for everyday signing. If you need stricter security or official certificates, GlobalSign and Adobe Acrobat support CA-authorized digital signatures that meet international compliance standards.
C. Which document security solution should you choose?

Choosing the right document security solution feels overwhelming. Here’s how to think about it:
1. Start with your biggest risk
Worried about forgery? Start with QR code document verification. It’s the fastest way to prove a document is real, tamper-free, and issued by you. Perfect for contracts, certificates, and anything official.
Concerned about external hackers? Focus on encryption and secure cloud storage to keep documents protected during transfer and while stored.
Dealing with insider risks? Prioritize access controls and audit trails so you know exactly who’s viewing, editing, or sharing sensitive files.
Your biggest risk should shape your first move. Handle that, and you’ll already be ahead of most.
2. Consider your industry requirements
Every industry has its own rules. If you’re in healthcare, you’re bound by HIPAA. That means strict data access, encryption, and patient privacy standards. If you’re in finance, you’re looking at SOX, PCI-DSS, or even GLBA compliance.
Pick security solutions that understand your world. Not all tools are built with compliance in mind. Look for ones that come with certifications or pre-built compliance frameworks.
3. Think about your team size
Small team? You need tools that are simple, fast, and don’t need a tech expert to run. Solutions like basic encryption and cloud storage with built-in permissions let you secure documents without slowing things down.
Bigger team? Go for systems that can scale and integrate. Think role-based access, audit logs, and tools that plug into your existing platforms like Microsoft 365 or Google Workspace.
4. Factor in your document types.
Not all documents need the same kind of protection. Legal firms sharing contracts need features like digital signatures, version control, and QR code verification to prove authenticity and prevent tampering.
A design agency, on the other hand, might care more about watermarking, restricted downloads, and view-only sharing to protect creative assets.
If you’re sending financial reports, client data, or IP, your setup should reflect that. Match the security tools to the type of content you’re handling. One size doesn’t fit all.
5. Don’t forget usability.
The fanciest security system fails if nobody uses it. If your team finds it clunky or confusing, they’ll default to risky workarounds like emailing files or turning off restrictions.
Pick tools that are clean, intuitive, and quick to learn. Even your least tech-savvy employee should be able to secure or verify a document without needing a walkthrough.
My advice? Start with one or two solutions and expand. Most businesses begin with encryption and access controls, then add features as they grow.
D. How QR verification is revolutionizing document security in 2025?
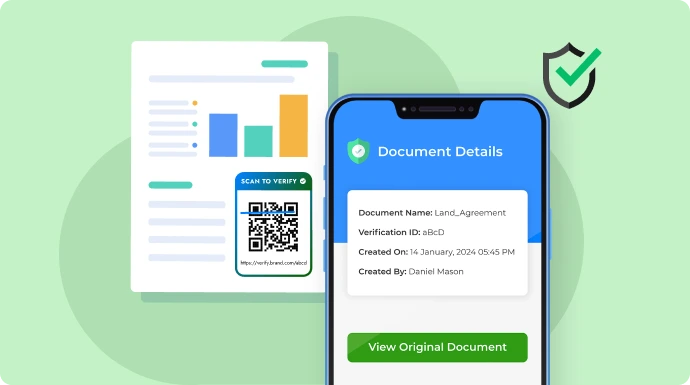
QR verification is transforming document security by solving a critical problem: how do you verify a document is real when anyone can fake signatures or alter PDFs?
The breakthrough is simple: QR codes create an unbreakable link between any document and its verified source. Unlike traditional security, that only protects digital files, QR codes work perfectly on printed documents too.
QR Mark pioneered this approach with security QR codes. Add a QR Mark code to any document, and it links directly to a secured source on your custom domain.
When someone scans the code with any smartphone camera, they’re taken to a verification page showing:
- Document owner’s name
- Official document name
- Creation date
- Unique document ID
The game-changer? The page also provides a downloadable copy of the original document. If there’s any doubt, recipients can download the verified version and compare. Or just use the fresh download, it’s guaranteed legitimate.
This system can also serve as part of a secure file sharing solution, giving both document owners and recipients confidence that what they’re accessing is authentic, tamper-proof, and from a trusted source.
This makes forgery practically impossible. Whether it’s a digital certificate or a printed contract, one scan reveals the truth. No special apps needed, no complex processes. Just point, scan, and verify.
The result? Document owners and recipients are protected from forgery with technology that actually works in the real world.
E. How can you create a document security audit checklist?

Creating a document security audit checklist helps you find weak spots before attackers do. Here’s how to build one that actually protects your business and supports document lifecycle security.
1. Start with access management
First, audit who can see your documents. Pull up your user list and check every name. You’d be surprised how many ex-employees still have access years after leaving. Also, verify permission levels match job roles, meaning interns shouldn’t have CEO-level access.
Look for shared accounts too. They’re massive security holes because you can’t track who did what. And actually test that multi-factor authentication works, don’t just assume it’s enabled.
2. Verify encryption status
Check if encryption is protecting the right documents. Many businesses encrypt stored files but forget about files being emailed or transferred. Don’t forget backups either – if main files are encrypted but backups aren’t, you’ve left a backdoor open.
Make sure multiple people know how to manage encryption keys. I’ve seen companies locked out of their own files because only one person had access.
3. Review compliance requirements
Match your security measures to industry regulations. Healthcare needs HIPAA compliance, financial services need SOX. But it’s not just about avoiding fines, it’s also about protecting data properly.
Test your deletion process too. When you delete files, do they actually disappear? Try recovering “deleted” files with recovery software. If you can get them back, so can hackers.
4. Assess technical security
Old software equals vulnerable software. Check when you last updated document security systems and install any patches. Test your defenses – are firewalls configured correctly? Does antivirus scan document uploads?
For cloud storage, review security settings carefully. Default settings are rarely enough for business documents.
5. Check physical security
Digital security fails if someone walks out with printed documents. Audit printer access, confidential documents shouldn’t sit in trays for hours. Verify you’re shredding sensitive papers, not tossing them in regular trash.
Check if the filing cabinets lock and whether visitors can access areas with sensitive documents. Physical breaches are still breaches.
6. Validate employee training
Employees make or break your security. Verify everyone completed training, but more importantly, test if they remember it. Send fake phishing emails about document access and see who clicks.
Check if staff understand which documents need extra protection and review password practices. “Password123!” won’t protect anything.
7. Test incident response
Run a mock breach drill. Tell your team sensitive documents leaked – do they know what to do? Who to call? How to lock down access?
Also, test backup restoration. Many businesses discover backups don’t work only when desperately needed. If ransomware hits tomorrow, make sure you can actually recover.
8. Assess third-party risks
Review everyone outside your company who accesses documents – vendors, contractors, partners. Check their security certifications and how you share files with them. Email isn’t secure enough for sensitive documents.
Many businesses use consumer-grade collaboration tools for business documents. That’s asking for trouble.
9. Making it work
Don’t audit everything at once, that’s overwhelming. Instead, focus on one area monthly. January for access management, February for encryption, and so on. This keeps security tight without burning out your team.
Document findings and set deadlines for fixes. A checklist is useless if you don’t act on discoveries. Remember, security isn’t a one-time thing – regular audits keep documents safe as threats evolve.
G. FAQs

1. What’s the difference between document security and cybersecurity?
Document security focuses specifically on protecting files and their contents. Cybersecurity is broader, covering networks, systems, and infrastructure. Think of document security as one important piece of your overall cybersecurity strategy.
2. How much do document security solutions typically cost?
Costs vary widely. Small business solutions typically start around $10–20 per user per month, including QR-based verification tools that help prevent document forgery right out of the box. . Enterprise document security can run $50-100+ per user, depending on features. Remember: the cost of a breach far exceeds the price of protection.
3. Can document security solutions work with my existing software?
Most modern tools are designed to fit into the systems you already use. If you’re working with Microsoft Office, Google Workspace, Dropbox, Salesforce, or other mainstream platforms, you’ll find plenty of document security solutions with built-in integrations or APIs. Look for ones that plug in easily without forcing a big change to your team’s workflow. Seamless adoption is key, especially if you’re trying to avoid pushback or delays.
4. How quickly can I implement document security solutions?
QR-based verification can be set up in just minutes. Basic cloud document security usually takes a few hours to get going. Full enterprise deployments may take 2–6 weeks, depending on how complex your setup is and how much customization you need. The best move is to start with your most critical documents, then expand as you go.
5. Do document security solutions slow down business processes?
Good solutions actually speed things up. While adding security steps might seem like it would slow work, modern systems automate so much that users often work faster. Automated classification, smart search, and streamlined sharing save more time than security checks consume.
The bottom line
Document security solutions aren’t optional anymore. They’re essential for protecting your business, maintaining compliance, and building customer trust.
The key is choosing solutions that match your needs. Start with your biggest vulnerabilities – maybe it’s encryption, perhaps it’s access control. Build from there.
Remember: the best document security solution is the one your team will actually use. Pick something powerful enough to protect you but simple enough that it doesn’t get in the way of work.
Your documents contain your business’s most valuable information. Protect them like the assets they are. Start today, because tomorrow might be too late.


Leave a Reply